At some point, you will find yourself asking – is my device actually running the code I expect it to? [bunnie] aka [Andrew Huang] is passionate about making devices you can fundamentally, deeply trust, and his latest passion project is the Precursor communicator.
At the heart of it is an FPGA, and Precursor’s CPU is created out of the gates of that FPGA. This and a myriad of other design decisions make the Precursor fundamentally hard to backdoor, and you don’t have to take [bunnie]’s word for it — he’s made an entire video going through the architecture, boot protections and guarantees of the Precursor, teaching us what goes into a secure device that’s also practical to use.

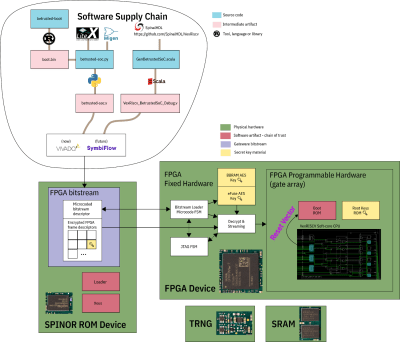 If you can’t understand how your device works, your trust in it might be misplaced. In the hour long video, [bunnie] explains the entire stack, from the lower levels of hardware to root keys used to sign and verify the integrity of your OS, along the way demonstrating how you can verify that things haven’t gone wrong.
If you can’t understand how your device works, your trust in it might be misplaced. In the hour long video, [bunnie] explains the entire stack, from the lower levels of hardware to root keys used to sign and verify the integrity of your OS, along the way demonstrating how you can verify that things haven’t gone wrong.
He makes sure to point out aspects you’d want to be cautious of, from physical security limitations to toolchain nuances. If you’re not up for a video, you can always check out the Precursor wiki, which has a treasure trove of information on the device’s security model.
As you might’ve already learned, it’s not enough for hardware to be open-source in order to be trustworthy. While open-source silicon designs are undoubtedly the future, their security guarantees only go so far.
Whether it’s esoteric hard drive firmware backdoors, weekend projects turning your WiFi card into a keylogger, or rootkits you can get on store-bought Lenovo laptops, hell, even our latest This Week In Security installment has two fun malware examples – there’s never a shortage of parties interested in collecting as much data as possible.

















….and you don’t have to take [bunnie]’s word for it….
Normally an independent audit follows such a precursor, not the same person doing an (in depth) explanation ;)
I think the point is, you can verify this yourself rather than take bunnies word for it. My memory is hazy but didn’t Bunnie do a lot of the research on hacking the Xbox 360?
Yes, and wrote an entire book about it!
Xbox, not the 360. The book linked below is well worth the read. Also the Chumby and other works.
Long love chumby
he was the first person to hack the og xbox while at MIT
I think I am staying within the target levels of paranoia if I point out that you only know what the device is running as long as all the required toolchains are also open source, which is not the case.
https://kakaroto.homelinux.net/2019/11/exploiting-intels-management-engine-part-2-enabling-red-jtag-unlock-on-intel-me-11-x-intel-sa-00086/
Especially since the device uses a typical FPGA which is a blackbox like any modern proprietary CPU.
So what does this device solve? It is small and portable. I could just use a Linux live iso on a read only medium to mount a dm-crypt/LUKS external storage and put my secrets in there.
https://github.com/betrusted-io/betrusted-wiki/wiki/FAQ:-FPGA-AES-Encryption-Key-(eFuse-BBRAM)#is-fpga-encryption-useless-due-to-the-starbleed-exploit
>if your primary threat model is someone physically confiscating your device and actively attacking it with your full knowledge, then no, the FPGA encryption won’t help you
>
Huh.
It’s not quite a black box. You have to read details to appreciate. It has some extremely obvious physical limitations that make it next to impossible to hide instructions/gates, and the fpga cpu gates can be randomized and checksummed in such a way that you can have high confidence that the fpga is only performing exactly what you think it to be. It is extremely well thought out and bunnie has some blog posts on exactly this concern and how it is mitigated. It’s practically entirely trustless!
prjxray project seems to have XC7S50 bitstream format figured out for the FPGA, so hopefully at some point in future there will be support in open source FPGA toolchains also.
Seems like it would be better to go have multiple smaller iCE40 FPGAs that are well understood (i.e. no secret or proprietary bits) and have an open toolchain rather than a giant SoC on FPGA that has a closed toolchain.
Alternatively, go with a CPU that is composed of hundreds of teeny-tiny CPUs with mere bytes of memory (similar to the GreenArrays chip) that must work cooperatively to do anything of interest. It should be possible to shuffle the CPU structure during runtime.
I don’t suppose you have seen anything of note done with those green array chips have you? I note that one could get maybe a hundred J1 CPUs on something like a De10 nano, and I presume they could all have a few K of ram rather than the smaller sizes in the GA chip, al9that did have 144 cores.
Privacy and open-source is a funny topic to discuss on HaD.
Yall ever read SupplyFrame’s privacy policy?
.. tracking and collecting personal info, doing reverse IP look-ups to find your personal info and see where you might work, correlate comments to IP or cookies, tracking cookies to monitor your other internet activity, giving full access to third-parties for them to place any cookies for any reason, buying your personal info from other sources, considering consent being you logged into a social media site when you visit HaD, selling your personal info to third parties..
The part where they discuss what they use your personal info for is about as unrestricted as it gets. I like that if you request your personal info be deleted, they only delete one copy. Ask to see how your info was used and they’ll probably ask for an image of your CA drivers license.
My personal understanding is, they’re a commercial company that has to analyze their audience so that they remain profitable and Hackaday stays afloat, that’s par for the course. Correlating comments to IP/cookies is a standard WordPress feature, and of course we’d rather have that, with such a large userbase – purely for moderation reasons. You have a wide variety of ways to set boundaries here, like adblockers that block scripts of your choosing, and they already block a lot of (if not all?) SF analytics by default. You can even disable JS on the .com pages!