
A fourth suspect has been arrested today for his role in the Twitter hack last year that gave attackers access to the company's internal network exposing high-profile accounts to hijacking.
The United States Department of Justice announced that Joseph O’Connor, a 22-year old UK national, was detained in Spain on several charges related to the Twitter hack in July 2020.
Tough life
The criminal complaint against O’Connor, filed in the U.S. District Court for the Northern District of California, alleges that the suspect was also involved in takeovers of TikTok and Snapchat accounts.
O’Connor’s role in the Twitter hack is unclear but he is now facing the following charges:
- three counts of conspiracy to intentionally access a computer without authorization and obtaining information from a protected computer
- two counts of intentionally accessing a computer without authorization and obtaining information from a protected computer
- one count of conspiracy to intentionally access a computer without authorization and, with the intent to extort from a person a thing of value, transmitting a communication containing a threat
- one count of making extortive communications; one count of making threatening communications
- two counts of cyberstalking
Three other suspects linked to the incident and indicted were Mason Sheppard (a.k.a. “Chaewon,” age 19), of Bognor Regis, U.K.; Nima Fazeli (a.k.a. “Rolex,” age 22) of Orlando, Florida; and Graham Ivan Clark (a.k.a. “Kirk,” of Tampa, Florida).
Kirk pleaded guilty and was sentenced to three years in prison. Florida State Attorney, Andrew Warren, considered Kirk the mastermind behind the entire incident.
O’Connor used the online aliases “PlugWalkJoe” and “j0e,” both aliases associated with a "notorious SIM swapper," KrebsOnSecurity wrote. Surprisingly, he did not hide his identity in an interview with the New York Times, just a couple of days after the hack. He even told journalists that he was British and located in Spain.
The four individuals charged for their role in the Twitter hack were part of a group that coveted accounts with short, special handles on various online platforms, which are typically reserved by the early users and referred to as O.G. (“original gangster”).
After obtaining credentials that allowed hijacking any Twitter account, the group started selling usernames (@dark, @w, @l, @R9, @50, or @vague) to the OGusers.com community.
At the time, O’Connor was a well-known dealer in the community. He told New York Times that he had learned from other hackers that Kirk had found the credentials giving access to the Twitter accounts on the company’s internal Slack communication channel.
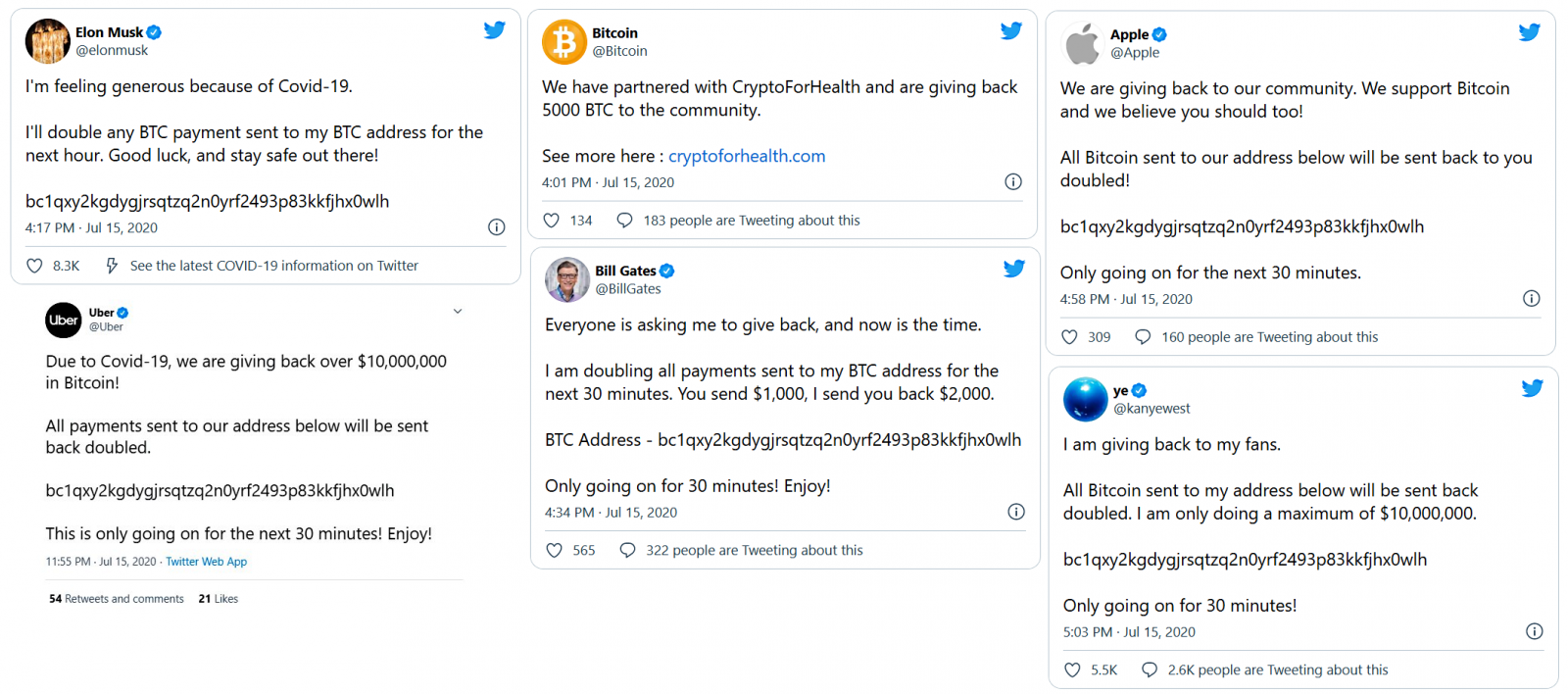
In total, the hackers hijacked 130 high-profile accounts counting those of politicians, celebrities, tech executives (@JeffBezos, @BarackObama, @elon_musk, @kanyewest, @JoeBiden, @BillGates, and @WarrenBuffet) and companies (@Apple, @Uber, @coinbase, @Gemini, @binance). They also read private messages from 36 of these accounts.
The group of hackers also used high-profile accounts to promote a cryptocurrency scam, managing to collect more than $100,000 in a single Bitcoin wallet.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now