Who said a sandbox is only for kids? Sandboxing is a security technique that is used to observe and analyze code in a secure and isolated fashion by impersonating the end-user operating environments.
Another use case of sandboxing is in the mitigation of cyber threats and malware injections as they are kept isolated to the sandbox, severed from the rest of the network.
But how does a sandbox work? What are the different types of sandboxing techniques and can a sandbox protect you online?
How Does a Sandbox Work?
Sandboxing is conducted by setting up an isolated test area or a "sandbox" that is ingested with malicious code or malware. The resulting behavior patterns are then observed and are classified as either "safe" or "unsafe" after the mock test is completed.
While most legacy security models operate on a reactive approach, sandboxing works proactively by observing both old and new patterns alike. This adds an extra layer of security and protects against many vulnerabilities like zero-day and hidden stealth attacks.
Both the cybersecurity and software development worlds use sandboxing as a standard practice but ensuring a fully isolated sandbox is more important for security purposes because the nature of malware is to continuously and aggressively scan networks for vulnerabilities.
An Example of an Online Sandbox
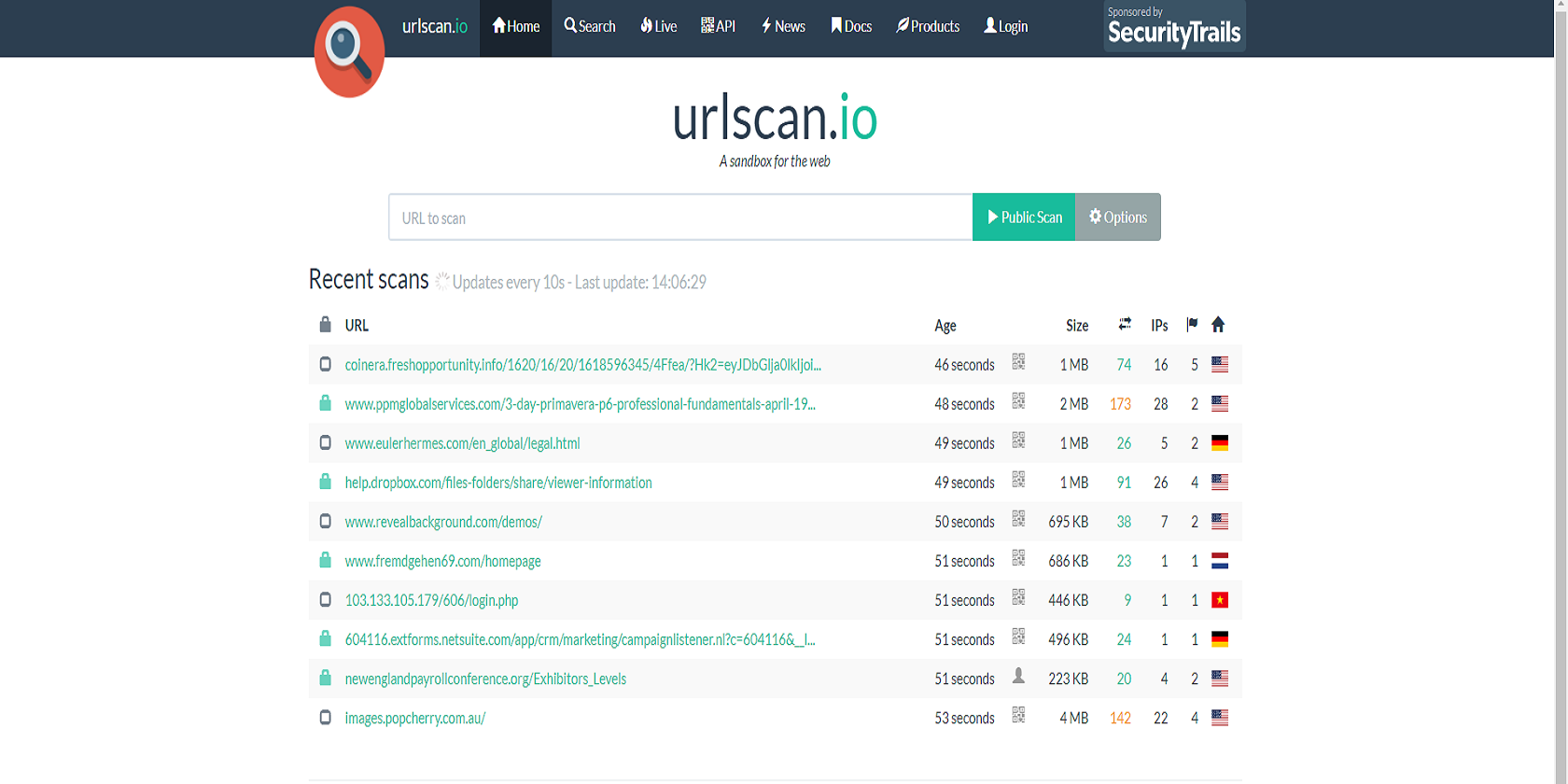
A great example of an online sandbox is a free service called urlscan.io that allows you to scan and analyze websites. Once you enter a potentially malicious URL on their website, an automated process will browse the URL, observe the behavior pattern, and will then pass a verdict on the URL.
Sandboxes like these are a win-win for all - not only are they accessible for free, but they also provide valuable and instantaneous feedback regarding the status of a URL.
Different Types of Sandboxing Techniques
The beauty of sandboxing is that it can be applied to anything - PCs, browsers, apps, even smartphones. Most firewalls, endpoint protection systems, and next-generation machine learning systems also utilize sandboxes as a threat deterrent.
Also, a sandbox can be both hardware and software-based and various versions and approaches are available depending on your needs and purpose. A developer working on new code will have different needs than an organization whose primary focus is to protect its OS from malicious attacks.
Here are the main types of sandboxing techniques.
Application-Based Sandboxing
Many applications use sandboxing by default to protect the local operating system. The Windows 10 operating system has a built-in sandbox to protect the desktop from unauthorized code. The Linux operating system also has several application sandboxes built on Seccomp and cgroup.
HTML5 also has a sandbox to protect against the misuse of its iframe feature and Java has its own sandbox, such as a Java applet running on a web page.
Google also offers a Sandbox API which is available to developers who write C++ code and need to sandbox it before deploying. While Apple has new sandbox security features that protect you from malicious iMessages.
Browser Sandboxing
Browsers are always at work and as such need extra security protection. Fortunately, most browsers of today come with built-in sandboxes where minimum end-user interaction is required.
Browser sandboxing is crucial in separating malicious applications that run on the internet from accessing local machines and their resources. Here are some of the major browsers and their sandboxing capabilities:
- Google Chrome has been sandboxed since its inception
- Opera is automatically sandboxed as it's built on Google’s Chromium code
- Mozilla Firefox offers selective implementations of sandboxing
- Internet Explorer introduced some level of sandboxing in 2006 with IE 7
- Microsoft Edge sandboxes each and every process now
- Apple’s Safari browser runs websites in separate processes
Developer Sandboxing
As the name implies, the main purpose of a developer sandbox is to test and develop code in an isolated environment. A developer sandbox usually includes a copy of a company's production metadata.
Cloud-Based or Virtual Sandboxing
A cloud sandbox is similar to a regular sandbox but the software is utilized in a virtual environment. This ensures full separation of URLs, downloads, or code from the network devices during and at the time of testing.
Sandboxing Protects You From Online Threats
Sandboxing truly helps in mitigating threats when you are online. Here are some major benefits of sanboxing.
Prevents Host Devices From Potential Threats
The biggest advantage of sandboxing is that it prevents your host devices and operating systems from getting exposed to potential threats.
Evaluates Malicious Software
Working with new vendors and untrusted software sources can be a potential threat waiting to attack. Sandboxing takes the threat factor out of such interactions by pre-emptively testing new software.
Tests Software Before Going Into Production
Sandbox can help with the launch of newly developed code by evaluating and testing it for potential vulnerabilities before it goes live.
Quarantines Zero-Day Threats
Sandboxing is a great technique for quarantining and getting rid of unknown exploits like zero-day threats. Many cloud-based sandboxing techniques can automatically quarantine such attacks and prevent further damages.
Integrates With Existing Security Strategies
In most cases, sandboxing can easily complement and integrate with existing security-based policies and products, offering you wide coverage for security protection.
Issues With Sandboxing
Just like other threat mitigation techniques, sandboxing also comes with a few downsides. Here are some common ones.
Resource Utilization
The biggest drawbacks of sandboxing can be extreme resource utilization and time consumption as setting up mock sandbox environments takes up extra time, effort, as well as resources.
Threats Can Sometimes Go Undetected
Sometimes threat actors can find evasive ways to fool a sandbox. For instance, cybercriminals can program a threat to stay dormant in order to pass the sandbox test.
Once the programmed malware detects that it is running inside a sandbox, it becomes inactive until it comes across a real endpoint device and then detonates.
Network Degradation and Increased Costs
In a sandboxed environment, every file entering the network will be introduced to the sandbox first. As great as it is for network security, it can certainly degrade network performance and increase operational costs.
Play in the Sandbox to Mitigate Threats
Online cyber threats and the risk of compromised credentials are increasing by the day. To curb these ever-evolving threats, existing security technologies need to be paired with evolving techniques like sandboxing.
By analyzing threats before they enter a system, sandboxing only allows safe files to pass through and quarantines the malicious ones. Where traditional security measures fail to discover new threats, sandboxing with its advanced threat detection features jumps in to help.
So go ahead, play in the sandbox and protect yourself from online threats.