
Security researchers are raising the alarm in regards to a new botnet named Satori that has been seen active on over 280,000 different IPs in the past 12 hours.
Satori —Japanese word for "awakening"— is not new, but a variant of the more infamous Mirai IoT DDoS malware.
Li Fengpei, a security researcher with Qihoo 360 Netlab, says the Satori variant came to life out of the blue today and started scans on ports 37215 and 52869.
Satori variant differs from previous Mirai versions
According to a report Li shared with Bleeping Computer today, the Mirai Satori variant is quite different from all previous pure Mirai variants.
Previous Mirai versions infected IoT devices and then downloaded a Telnet scanner component that attempted to find other victims and infect them with the Mirai bot.
The Satori variant does not use a scanner but uses two embedded exploits that will try to connect to remote devices on ports 37215 and 52869.
Effectively, this makes Satori an IoT worm, being able to spread by itself without the need for separate components.
Growth fueled by mysterious Huawei exploit (zero-day?)
Li says that telemetry gathered by Netlab's infrastructure has observed 263,250 different IPs scanning port 37215, and 19,403 IPs scanning port 52869 in the last 12 hours. That's over 280,000 bots in the last half of day.
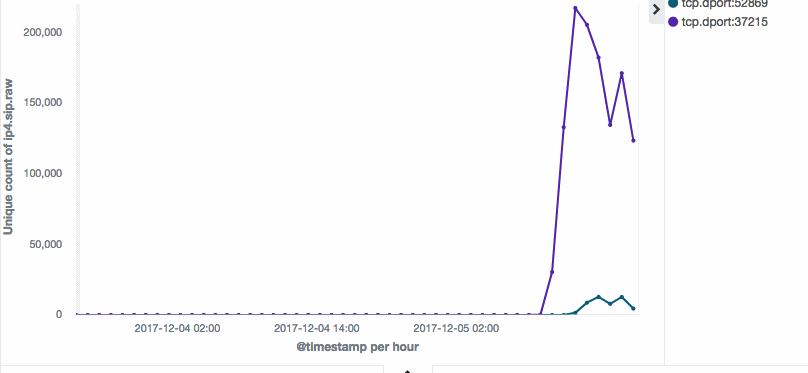
A botnet reaching this huge size is of note. Satori's success is in large part due to the exploit it delivers on port 37215. According to Li's description, this appears to be a zero-day.
"The one on port 37215 is not fully disclosed yet, our team has been tracking this in the last few days and got quite some insight, but we will not discuss it," Li said.
Dale Drew, chief security strategist at broadband Internet provider CenturyLink, told ArsTechnica in an interview published earlier today that he believes this botnet abuses a zero-day in Huawei Home Gateway routers, a remote code execution bug noticed by Check Point at the end of November, about which very few details are available.
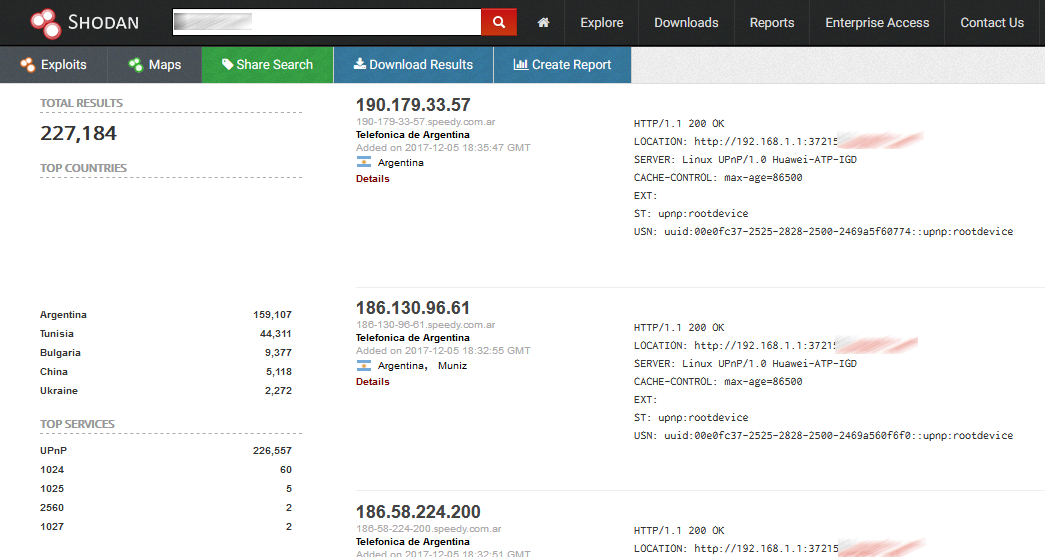
A security researcher shared details with Bleeping Computer about the possible exploit, and a Shodan search for affected devices yields over 225,000 devices that are currently available online.
As for the other exploit, on port 52869, this is for a known and old vulnerability in Realtek devices (CVE-2014-8361), one that was most likely patched in some devices, hence the reason why scans for this exploit are less successful.
Satori has connections to a previous Mirai botnet
Li also points out that there are clues to link the botnet created with the Mirai Satori variant with another Mirai-based botnet Netlab has seen last month, and which reached around 100,000 bots, most located in Argentina.
It is unclear if the same person runs both botnets, but Li says the current Mirai Satori variant and the previous Mirai-based variation shared file names and static features, and some of the C2 protocols.
A security researcher told Bleeping Computer today that they too believe the two botnets to be related, with Satori evolving from last month Mirai variant.
Right now, security researchers are still gathering information on this new threat, but public honeypot data confirms Netlab's report [1, 2, 3, 4].


Comments
Woolool - 6 years ago
The botnet makers are weebs.
Getwebhawk - 4 years ago
Thanks for sharing this valuable post with us