![]()
Modern-day ships aren't that hard to hack according to Ken Munro, a security researcher at Pen Test Partners, a UK cyber-security company.
Speaking at a conference in Athens, Greece, Munro detailed some of the most appalling security lapses he found while investigating naval ships that had equipment exposed online.
His research focused on using basic tools, known by all capable security researchers, but also threat actors alike.
Just by using Shodan, a search engine that identifies anything connected to the Internet, Munro found ship equipment all over the world, but sadly, not all of it was properly configured.
The good ol' admin/1234 account
Some of the most sensitive equipment he found were satellite antennas mounted on ships to provide around the clock radio, Internet, GSM, and other communications.
One such model was the Cobham Sailor 900, for which exists a public exploit that makes hacking it a child's play for any knowledgeable attacker.
In many cases, the exploit wouldn't even be needed, as the equipment used the same default password — admin/1234 — as both Munro and French security researcher X0rz have pointed out.
The bad news is that these antennas aren't only found on ships, but also helicopters and airplanes. In addition, you won't only see these antennas on container and passenger ships, but also on navy and private security boats.
Some devices failed harder than others
Other equipment that Munro found incorrectly configured and exposed online include Globe Wireless satellite antennas or KVH CommBox private network terminals.
Both handled logins via HTTP, but worse was CommBox, which also leaked the vessel's name on the login page, and even had a button that listed all active users, allowing an attacker access to the names of all of the ship's crew.
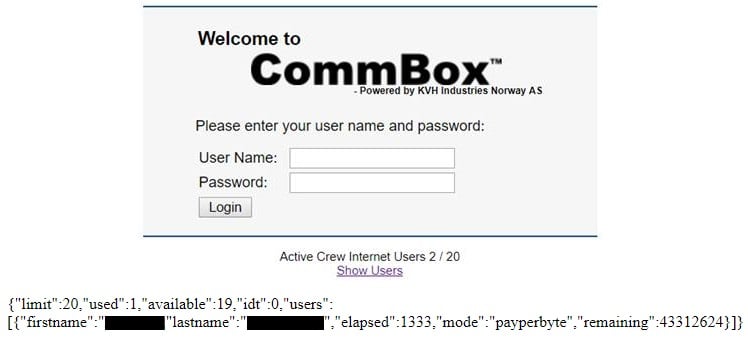
Furthermore, an attacker could get in-depth details about the private network just by hovering the mouse over certain elements on the login page. Such details should have been placed behind the login page, and not on it.
There have been no reported incidents of ship satcom hacking until now, but this is only a matter of time.
So far, some confused malware authors didn't realize what they were doing and ended up installing remote access trojans on some satcom systems.
XtremeRAT installed on a VSAT provider IP range #malware #VSAT https://t.co/uYkWhjnfwI
— x0rz (@x0rz) July 24, 2017
Munro's research into this topic is certainly not new, as Rapid7 has already covered it in a similar report in 2013. What Munro points out is that now, the number of exposed ships has gone up.
Munro: Ships are ICS, but floating
The expert likens ships to industrial control systems used to control machinery in plants and factories. As the Internet era rolled in, most companies exposed these systems to the Internet without thinking their actions through and taking the necessary security precautions.
Back in the day, ICS ran on dedicated, isolated networks. Network protocols were custom and arcane, security was non-existent in these safety critical systems. [...] Now ships: complex industrial controls, but floating. Traditionally isolated, now always-on, connected through VSAT, GSM/LTE and even Wi-Fi. Crew internet access, mashed up with electronic navigation systems, ECDIS, propulsion, load management and numerous other complex, custom systems. A recipe for disaster.
The researcher is advocating for the introduction of basic security policies in modern ships. First and foremost, while there are multiple types of equipment found on a ship that connect online, Munro says that satellite antennas must be secured first, above all.
"There are many routes [of attack] onto a ship, but the satcom box is the one route that is nearly always on the internet. Start with securing these devices, then move on to securing other ship systems," Munro says.
The researcher says this can be done by changing default passwords, using complex passwords for all user accounts, and TLS for protecting login fields. After that, updating the firmware to the latest version is a must.
"It’s simply not acceptable to leave vanilla firmware in place," the expert says.
In July of this year, Shodan also set up a website that uses equipment exposed online to track ships as they move across the globe. The project is named Ship Tracker.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now