A Russia-speaking malware developer going by the name of "TheBottle" has started selling a new infostealer with the name of Ovidiy Stealer.
This new malware strain is offered for sale on a Russian website for 450-750 Rubles ($7-$13). The low price is because the malware isn't as powerful as other commercial infostealers available on the market.
TheBottle started selling his new tool about a month ago and has also advertised it on various cybercrime forums.
Ovidiy Stealer spread via malicious EXE files
The malware would have gone undiscovered if its buyers wouldn't have used it to infect various users. Proofpoint researchers spotted the malware during the past weeks distributed as booby-trapped executable masking as various legitimate applications. Below is a list of filenames that were used to distribute Ovidiy Stealer during the past month:
HideMiner.zip
VkHackTool.zip
update_teamspeak3.5.1.exe
WORLD OF TANKS 2017.txt.exe
dice_bot.exe
cheat v5.4.3 2017.exe
Vk.com BulliTl.exe
These files were spread via file hosting portals, cracking & keygen sites, but also via email campaigns that delivered the file as an attachment, or included a link where users could download the file.
Files infected with this infostealer have a low detection ratio on VirusTotal and are usually marked with generic names, a problem in Proofpoint's opinion.
"It is possible that an AV solution will detect the behavior of Ovidiy Stealer but label it in logs with a generic description and thus [Security Operations Center] analysts monitoring alerts may well see the event but not recognize its significance," researchers said in a technical report.
Ovidiy Stealer has limited features, but it's more than enough
Infected hosts should be aware that Ovidiy Stealer can collect and steal information from applications such as:
Google Chrome
Kometa browser
Amigo browser
Torch browser
Orbitum browser
Opera browser
Once antivirus solutions will update their definitions and detect Ovidiy Stealer correctly, infected hosts should reset passwords for all the online identities stored in the above applications.
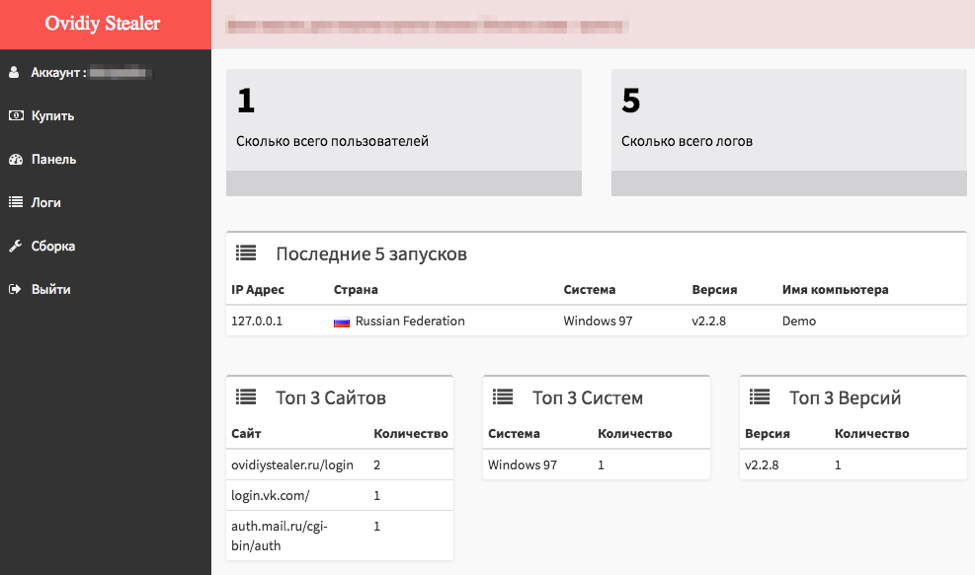
All information stolen from victims is sent to a control panel to which the malware's buyers have access to. This backend is stored on the same server that hosts the tool's website, at ovidiystealer.ru.
This is a rookie mistake on the malware's author part. Authorities can take his website down, or competitors can launch DDoS attacks, crippling his operation.
TheBottle has also made other mistakes. For example, all payments for Ovidiy Stealer are handled via RoboKassa, a PayPal-like money processor based in Russia. These transactions could be tracked to the author's real-life identity.
Ovidiy Stealer doesn't obtain boot persistence
Furthermore, at the technical level, the tool is also incomplete. Besides targeting only a few applications, compared to other commercial infostealer, Ovidiy also lacks the ability to persist between PC reboots.
Nonetheless, this feature is not really needed for an infostealer, which needs only a few seconds to dump and steal the user's data. Boot persistence is more important for banking trojans, RATs, and keyloggers, compared to infostealers.
"While it is not the most advanced stealer we have seen, marketing and an entry-level price scheme make it attractive and accessible to many would-be criminals," Proofpoint researchers conclude in their report. "Ovidiy Stealer is lightweight and simple enough to work with relative ease, allowing for simple and efficient credential exfiltration. A lightweight, easy-to-use, and effective product coupled with frequent updates and a stable support system give Ovidiy Stealer the potential to become a much more widespread threat."
IOCs are available in Proofpoint's report.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now