Experts from security firm Wordfence say they have observed a wave of web attacks that took aim at unfinished WordPress installations.
These are sites where a user had uploaded the WordPress CMS, started but never finished the installation process.
These sites remained open to external connections, and anyone could have accessed their install panel and complete the installation on behalf of the user.
Mass scan detected looking for unfinished WordPress sites
According to Wordfence, this is exactly what happened. For almost a month, starting with the end of May and through mid-June, an attacker had mass-scanned the Internet for WordPress installations that still featured their installation file.
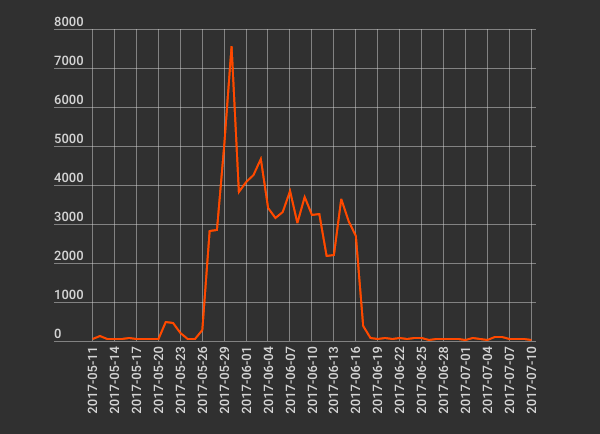
Mark Maunder, Wordfence founder and CEO, says his company observed one threat actor connecting to these unfinished WordPress sites, entering his own database credentials, and completing the installation process.
The attacker would then connect to the site using his newly created admin account, and use the theme or plugin file editor to insert malicious code and execute it, effectively taking over the victim's server. In another twist of this attack, the intruder also installed a custom plugin that executed the same malicious code.
Maunder named these attacks as "WPSetup Attack," and is advising users to make sure they finish a WordPress installation process right after they upload their CMS files on their server, as a new wave of these scans could trigger at any moment.
Statistics for attacks on WordPress sites
In a report released a day later after the WPSetup Attack alert, Wordfence also said that during the month of June, attacks on WordPress sites have gone up compared to the previous month.
Below are some of the main points from Wordfence's June 2017 WordPress Attack Report:
⇾ Brute force attacks made up 67% of total attacks for June, up from 72% in May. Complex attacks accounted for 33%.
⇾ Ukraine had the most IPs on the top 25 list with 7, followed by the United States with 7.
⇾ The average number of daily brute force attacks increased 36% from last month.
⇾ Average daily attack volume for June was up 32% from May, at 7.2 million.
⇾ Attack volume was quite a bit higher in the second half of the month, peaking at over 11 million attacks in a single day.
⇾ The most attacked WordPress theme was mTheme-Unus
⇾ The large majority of the attacks on all of the themes are attempts to exploit a well known vulnerability in a PHP file they all shared that was publicly disclosed a few years ago.
⇾ Almost 98% of these attacks on WordPress themes originate from just two IP addresses: 194.28.115.252 and 194.28.115.228.
⇾ The most attacked WordPress plugin was WP Mobile Detector.
Most attacks on WordPress sites came from Russian IP addresses, followed by the US and Ukraine.


Comments
Occasional - 6 years ago
I'm sure most of the internet security professionals setting up a WP site will take note, and avoid that trap. Now, is there anyone else that needs to be told?