IBM has issued a security alert last week, warning customers that some USB flash drives shipped with IBM Storwize products may contain malicious code.
The USB flash drive is said to store the Initialization Tool for IBM Storwize, a big data storage system (rack-based disks system) for data centers.
The part number of the infected flash drives is 01AC585. IBM says these USB sticks have been shipped with products such as:
- IBM Storwize V3500 - 2071 models 02A and 10A
- IBM Storwize V3700 - 2072 models 12C, 24C and 2DC
- IBM Storwize V5000 - 2077 models 12C and 24C
- IBM Storwize V5000 - 2078 models 12C and 24C
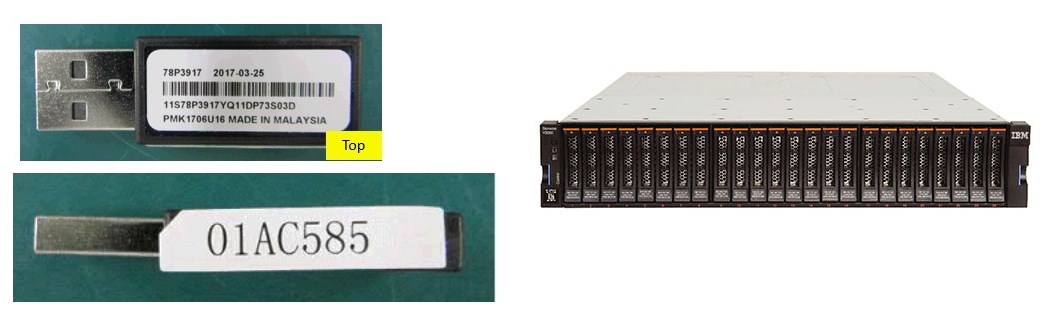
"Neither the IBM Storwize storage systems nor data stored on these systems are infected by this malicious code," said IBM.
Furthermore, USB flash drives used for Encryption Key management, which also ship with Storwize equipment, are not affected by this issue.
Malicious code is copied, but not executed
According to IBM, when users run the IBM Storwize Initialization Tool, the malicious code is copied, along with the rest of the Initialization Tool, on the user's device. The location where this data is copied is:
On Windows systems: %TMP%\initTool
On Linux and Mac systems: /tmp/initTool
IBM says the malicious code is only copied to user devices, but not executed. The company didn't provide details about the nature of this malicious code, or how it got on its USB flash drives, but based on current detections on antivirus engines, this appears to be a basic malware downloader.
The MD5 hash of the malicious file is 0178a69c43d4c57d401bf9596299ea57, and most antivirus vendors already detect it under various names.
| Engine | Signature | Version | Update |
| AhnLab-V3 | Win32/Pondre | 3.8.3.16811 | 20170330 |
| ESET-NOD32 | Win32/TrojanDropper.Agent.PYF | 15180 | 20170331 |
| Kaspersky | Trojan.Win32.Reconyc.hvow | 15.0.1.13 | 20170331 |
| McAfee | PWSZbot-FIB!0178A69C43D4 | 6.0.6.653 | 20170331 |
| McAfee-GW-Edition | PWSZbot-FIB!0178A69C43D4 | v2015 | 20170331 |
| Microsoft | VirTool:Win32/Injector.EG | 1.1.13601.0 | 20170331 |
| Qihoo-360 | Virus.Win32.WdExt.A | 1.0.0.1120 | 20170331 |
| Symantec | W32.Faedevour!inf | 1.2.1.0 | 20170330 |
| Tencent | Trojan.Win32.Daws.a | 1.0.0.1 | 20170331 |
| TrendMicro | PE_WINDEX.A | 9.740.0.1012 | 20170331 |
| TrendMicro-HouseCall | PE_WINDEX.A | 9.900.0.1004 | 20170331 |
| ZoneAlarm | Trojan.Win32.Reconyc.hvow | 1 | 20170331 |
IBM recommends formatting USB sticks
The company recommends that Storwize customers scan their system for the aforementioned folders and remove the directories.
Once the malicious code has been removed from infected devices, IBM recommends that users format their USB flash drive, download a safe copy of the Storwize Initialization Tool, and unzip its content on the original USB flash drive.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now