
This article was originally published on Scott Helme's blog and is reprinted here with his permission.
I was recently invited to take part in some research by BBC Click, alongside Professor Alan Woodward, to analyze a device that had quite a lot of people all excited. With slick marketing, catchy tag lines and some pretty bold claims about its security, nomx claims to have cracked e-mail security once and for all. Down the rabbit hole we go!
nomx
You can find the official nomx site at nomx.com and right away you will see how secure this device is.
"Everything else is insecure."
"The world’s most secure communications protocol..."
"nomx ensures absolute privacy for personal and commercial email and messaging..."
"DID YOU KNOW THAT EVERY SINGLE MAJOR EMAIL PROVIDER HAS BEEN HACKED?"
That's a lot of pretty big claims for such a small amount of space on the homepage so I was more than happy to get involved in investigating the device. I met with the BBC in London and they provided the retail packaged device that was to become mine for testing purposes. It's pretty nice looking with some fancy packaging—and you'd hope so, too, with a starting price of $199!
Starting the investigation
Before I even powered on the device, the first thing I wanted to do was open it up and see what was inside the case. If possible it'd be nice to take a backup of any flash storage or firmware on the device to have a backup that I could revert to if I break something, and also a reference point of how the device was when I received it if needed. I flipped it over and started to open up the case, expecting to find a fairly basic PCB inside. It had micro-USB for power and an Ethernet port on the side, with the box measuring 14cm x 14cm (5.5" x 5.5").
Now, as soon as I looked at this device I already had a really bad feeling. First of all, through the vent holes on the top I could see that the PCB inside took up about 25 percent of the footprint of the device, the case was considerably larger than the PCB inside it, which seemed odd. Second, the MAC address on the bottom looked familiar, really familiar. Putting that little thought to the back of my mind I cracked open the case by removing the standard screws in the bottom to confirm my initial suspicion.
Turns out that MAC address was really familiar because the prefix is from the Raspberry Pi Foundation. They own the <code>B8-27-EB</code> assignment, which you can search for on the IEEE site. Select 'MAC Address Block Large (MA-L)' from the drop down menu and filter on 'Raspberry.'
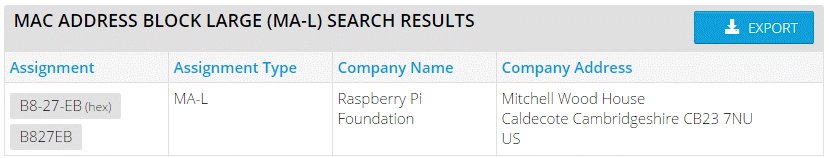
To be clear, I have absolutely no problem with the Raspberry Pi at all. It's an awesome little device and I've used it in a few projects of my own. I wasn't however expecting to find one nestled in the corner of a large box that claims to provide a completely secure and proprietary e-mail protocol! Because the device is just a Raspberry Pi, under the hood that made taking a backup really easy. I simply popped out the Micro SD card and put it in my card reader and used Win32DiskImager to take a full clone of the card.
Firing up the device
Now that I had a backup of the memory card, I could go to town on the device itself and not worry about causing irreparable damage. In the worst case scenario I could always flash back to a stock image and start again without any problems. Knowing it was an rPi, I grabbed a spare monitor and keyboard and decided to hook straight up to the device and boot it, I was pretty surprised when it started booting into Raspbian. Once I hit the login prompt I tried the default creds, to no avail. I then took a few shots at the root password, but no joy. It's pretty easy to reset the root user password on an rPi, though, so I took the card out, tinkered with it on my PC, and booted it back up again to a root shell.
Yes, there are a few things to be concerned about in those images, but the main point is I had a root shell so I could reset the root user password and SSH in to the rPi from my main PC instead of using a crappy monitor and keyboard. I dropped my SSH key in there and also fired up WinSCP from my desktop to take a full dump of the OS contents to work with. The device was running Nginx so I wanted to look where the Web root was to browse through the source, and I also saw a couple of other programs starting on boot—programs like Dovecot and Postfix. There were quite a few interesting things to look through!
Old software
I wanted to see exactly what was running on the device, so I did a quick run down of the software that was installed and how it was configured. Here's the list of what I could find:
- Raspbian GNU/Linux 7 (wheezy)—last updated 7th May 2015
- nginx version: nginx/1.2.1—released 5th June 2012
- PHP 5.4.45-0+deb7u5—released 3rd September 2015
- OpenSSL 1.0.1t—released 3rd May 2016
- Dovecot 2.1.7—released 29th May 2012
- Postfix 2.9.6—released 4th February 2013
- MySQL Ver 14.14 Distrib 5.5.52—released 6th September 2016
It's interesting to see such outdated versions of software on there. If the device was built even remotely recently, I'm not sure how you'd end up with such seriously old versions installed. I had a look for any auto-update mechanism that I could find but couldn't see anything on there. I thought perhaps the device would trigger some kind of update later when I go through the setup in the Web interface, so all may not be lost just yet. For now, it was interesting to know that everything on there seemed to be pretty standard for your everyday mail server. There were certainly no hints of anything proprietary.
Server setup
After my quick dig around at the command line I decided to open up the browser and go through the setup process. You have to get the IP of the device from your router or DHCP server and connect to it in the browser.
We can't log in just yet, though, as we don't have an account on the device. So we have to manually navigate to the Setup page...
Further down the setup page we can create our own 'superadmin' account and all we need is the setup password.
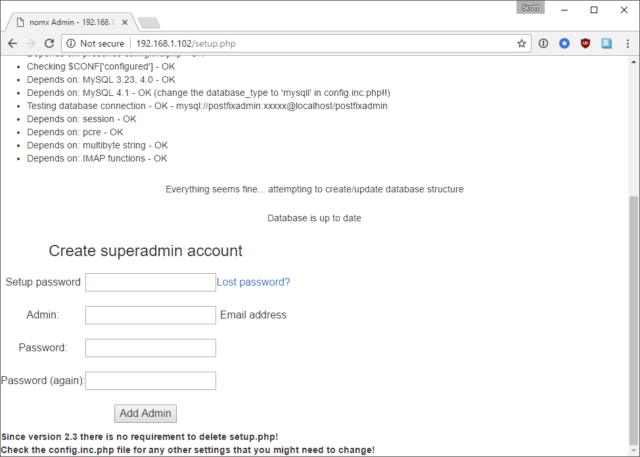
The only problem is I couldn't find the setup password anywhere so I had to hit the lost password link. This prompts me to create a new setup password and then instructs me to edit a PHP file on the device and paste the password in there!
Now, I'm not sure how someone is supposed to edit this PHP file right now because I can't see the SSH instructions anywhere. Nor can I see the setup password anywhere, either. To save you all the trouble, I extracted the hash of the original password whilst I had SSH access and you can see it here:
ec949c6a38322f160e8975cea965b4f6:1b84261e5d578c248825a58512175fa17d2bc118
It turns out this was pretty easy to break after I had a quick dig in the source to see how they generated the hash.
function generate_setup_password_salt() {
$salt = time() . '*' . $_SERVER['REMOTE_ADDR'] . '*' . mt_rand(0,60000);
$salt = md5($salt);
return $salt;
}
function encrypt_setup_password($password, $salt) {
return $salt . ':' . sha1($salt . ':' . $password);
}
Soooo, yeah. I also had a dig around in the config file and stumbled over this which is used during the setup process.
$CONF['min_password_length'] = 5;
Anyway, the main point for now was that I managed to crack the setup password, which was death, with a quick tweet asking for help. I could have set my own if I needed so I could create an account and log in to the device.
Configuration
With my 'superadmin' account created I could now begin the process of setting up my unhackable (not) e-mail server. Interesting that my browser thinks the login page isn't secure, huh?
Once logged in the site is pretty barren and the only real option is to add my new domain that will be used for my e-mail address.
So I followed through the instructions and hit the 'New Domain' button where I was presented with the following screen:
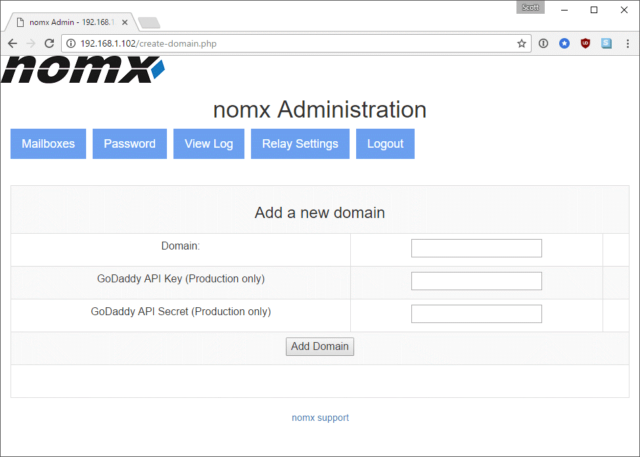
I've no idea why the device can only support domains purchased through GoDaddy, but I followed the instructions and purchased my domain, inserting the API keys into the screen as requested.
At this point I won't bore you with the rest of the terrible Web interface but you setup a few mailboxes with credentials that can then be configured in your favorite mail client. Everything seems pretty darn standard for "The world's most secure communications protocol." The setup instructions also ask me to open the following series of ports in my router and forward them to the nomx device:
- port 26 / TCP
- port 465 / TCP
- port 587 / TCP
- port 993 / TCP
- port 995 / TCP
These must be the ports for their protocol! (Hint: these are standard e-mail server ports) So, I decided to set my e-mail account up in Thunderbird and sure enough, it didn't work. I couldn't for the life of me get this thing to work properly, even just sending a basic e-mail, until I realized that they don't ask you to open port 25 in the instructions—which is required as the standard SMTP port! I will detail more on what port 26 is for later, but once I opened up port 25 I could at least send and receive e-mail. Well, I could almost send and receive e-mail.
reader comments
175