Abstract
This article applies social network analysis to a case study to analyze the role of madams in an Nigerian sex trafficking network. Using relational data on telephone conversations, the main centrality measures are calculated. They are interrelated with the roles of all the members of the network. The analysis confirms the importance of madams already highlighted by many academics, but surprisingly it also shows that not all madams are equally central in terms of their brokerage positions. Indeed, two different groups of madams are identified according to their betweenness centrality, which is the measure that best reveals the strategic positioning of the nodes within a network. The content analysis and description of the madams’ ego networks demonstrate that the main requirements for occupying a brokerage role are (i) being able to operate also outside Italian borders, and (ii) being at the same time part of relational systems involving “transnational” people whose action extends beyond national borders.





Similar content being viewed by others
Notes
According to the UNODC (2010:16), the value of the market associated to sex trafficking in Europe is about three billion dollars every year. Specific data about the earnings of the Nigerian traffickers are not available, but a lot of money transfers have been registered from Europe to Nigeria (especially to the Edo State) (UNODC/UNICRI 2003).
In general, the loan amounts to 50,000–60,000 euros. It is accepted by the victim and by her family because they do not have a clear idea of what this amount of money signifies (Prina 2003).
There are different kinds of voodoo ritual. In general, they are performed using hair, pubic hair and nails of the victims, which are wrapped in paper together with organic material from animals or vegetable extracts (Prina 2003).
The force of these rituals derives from the magic-religious belief widespread in Nigeria that if the pledges are not observed the victims may fall ill, die or something evil may happen. As van Dijk writes (2001:565), “‘Voodoo’ was defined as an essential element in how the system was operated by women traders and traffickers”.
What they do not know are the working conditions (management of time and money, restricted freedom of movement, subjection to the madam and so on) (Aghatise 2001).
Three main types of journey can be identified (Prina 2003): an air journey whose direct destination is a Western Europe country (Paris, London, Amsterdam, and so on) and then arrival in Italy by train or car; an air journey with stopovers in Eastern Europe (Prague, Budapest, Warsaw, Turkey, and so on); and an overland journey.
72 % of African victims detected by law enforcement in Italy from 2003 to 2007 were Nigerian (UNODC 2009b:42) and Nigerian nationality is the most frequent among victims assisted in Italy.
The analysis has been performed using Ucinet 6 software (Borgatti et al. 2002).
This study has analyzed only the telephone calls made by the actors, which have been considered the best data to understand the relationships between the actors and their centrality. Indeed, telephone represents the main communication medium which has been used also to plan the physical encounters.
Data have been considered as symmetric values because in many cases it was not possible to identify the direction of the telephone calls.
The graphical representations have been produced using the Net Draw program (Borgatti 2002).
In particular, these studies (Morselli 2010; Calderoni 2011) have analyzed the relation between centrality measures and vulnerability of the actors during law enforcement investigations. They show that the people who seem to have the most central role in the network are often not the most important ones: they are involved in numerous conversations and hence have a higher probability of being wiretapped and arrested, but this does not reflect their status within the network.
The density by group associated with gender (males 34; females 52) shows that females register the highest percentage of density. In particular, they have 2.3 % of the possible ties with the males and 5 % of the possible ties with the females. Considering nationality (not specified 8; Nigerian 73; Italian 5), the Nigerians have 3.6 % of the possible ties with their co-nationals, while the Italians and the people whose nationality was not stated are less present in the telephone calls. However, non-Nigerians register their highest percentages (respectively 2.5 % and 1.4 %) with Nigerians. This means that the Nigerians and the women were at the centre of the communication flows.
If the N16 and N24 nodes are excluded from the analysis, the value of R2 decreases to 0.2884, showing a very low correlation.
Some studies have shown that people with a strategic positioning in the network are likely to have lower degree and higher betweenneess centrality scores. This pattern assures them control over the information and the activities while at the same time being at less risk of detection (Baker and Faulkner 1993; Morselli 2009a and b; Morselli 2010).
The table reporting the information on all nodes is available in the Annex.
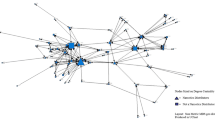
In particular, a key position in the network was performed by the person responsible for control N10. As can be seen in Fig. 1, she acted as a link between two parts of the network.
References
Aghatise E (2001) Research and case studies on the international trafficking of Nigerian women and girls for prostitution in Italy. Associazione Iroko, Turin
Aghatise E (2002) Trafficking for prostitution in Italy: concept paper. Paper presented at the Expert Group Meeting on Trafficking in women and girls, Glen Cove, New York November 18–22 2002. Retrievable at: http://www.un.org/womenwatch/daw/egm/trafficking2002/reports/EP-Aghatise.PDF
Aghatise E (2004) Trafficking for prostitution in Italy: possible effects of Government proposal for legalization of brothels. Violence Against Women 10(10):1126–1155
Aronowitz A (2001) Smuggling and trafficking in human being: the phenomenon, the markets that drive it and the organizations that promote it. Eur J Crim Policy Res 9:163–195
Aronowitz A (2009) Human trafficking, human misery. The global trade in human beings. Praeger Publishers, Westport
Aronowitz A, Peruffo M (2004) Trafficking in human beings and related crimes in West and Central Africa. In: Sumner C (ed) The Blackwell companion to criminology. Blackwell Publishing Ltd, Malden
Baker WE, Faulkner RR (1993) The social organization of conspiracy: illegal networks in the heavy electrical equipment industry. Am Sociol Rev 58(6):837–860
Becucci S (2003) Mercati criminali fra arcaismo e modernità. In: Becucci S, Massari M (eds) Globalizzazione e criminalità. Laterza, Bari
Becucci S (2008) New players in an old game: the sex market in Italy. In: Siegel D, Nelen H (eds) Organized crime: culture, markets and policies. Springer, New York
Borgatti SP (2002) Netdraw network visualization. Analytic Technologies, Harvard
Borgatti SP, Everett MG, Freeman LC (2002) Ucinet 6 for Windows: software for social network analysis. Analytic Technologies, Harvard
Borgatti SP, Mehra A, Brass D, Labianca A (2009) Network analysis in the social sciences. Science 323(5916):892–895
Bosco F, Di Cortemiglia VL, Serojitdinov A (2009) Human trafficking patterns. In: Friesendorf C (ed) Strategies against human trafficking: the role of the security sector. National Defence Academy and Austrian Ministry of Defence and Sports, Vienna
Bright DA, Greenhill C, Levenkova N (2011) Dismantling criminal networks: can node attributes play a role? Paper presented at the Third Annual Illicit Networks Workshop, Montreal, October 3–4 2011. Retrievable at: http://www.erdr.org/textes/bright_greenhill_levenkova.pdf
Calderoni F (2010) The ‘Ndrangheta through the lens of social network analysis: a tale from Calabria. Paper presented at the Crime and Social Institutions, 62nd Annual Meeting of the American Society of Criminology, San Francisco, November 17 2010
Calderoni F (2011) Strategic positioning in Mafia networks. Paper presented at the Third Annual Illicit Networks Workshop, Montreal, October 3–4 2011
Caneppele S, Mancuso M (2012) Are protection policies for human trafficking victims effective? An analysis of the Italian case. Eur J Crim Policy Res. doi:10.1007/s10610-012-9188-9
Carchedi F, Tola V (2008) All’aperto e al chiuso. Prostituzione e tratta: i nuovi dati del fenomeno, i servizi sociali, normative di riferimento. Ediesse, Roma
Carling J (2004) Migration, human smuggling and trafficking from Nigeria to Europe, International Organization for Migration–International Peace Research Institute, Oslo (PRIO). Retrievable at: http://iom.int/jahia/webdav/site/myjahiasite/shared/shared/mainsite/published_docs/serial_publications/mrs23.pdf
Carrington PJ (2011) Crime and social network analysis. In: Scott JP, Carrington PJ (eds) The SAGE handbook of social network analysis. SAGE Publications, London
Chattoe E, Hamill H (2005) It’s not who you know. It’s what you know about people you don’t know that counts: extending the analysis of crime groups as social networks. Br J Criminol 45(6):860–876
Cockbain E, Brayley H, Laycock G (2011) Exploring internal child sex trafficking networks using social network analysis. Policing 5(2):144–157
Eckberg GS (2007) Prostitution and trafficking in women: basic concepts. Paper presented at the International Conference on Human Trafficking and Prostitution, Benin City, March 26–28, 2007
Ekeoku NI (1986) Government external borrowing in the Nigerian post-boom era: some simulation results and implications, Nigerian. J Econ Soc Stud 28(3):357–369
Europol (2011) Trafficking in human beings in the European Union. European Police Office, Aja
Finckenauer JO (2001) Russian transnational organized crime and human trafficking. In: Kyle D, Koslowski R (eds) Global human smuggling: comparative perspectives. The Johns Hopkins University Press, Baltimore
Fitzgibbon K (2003) Modern day slavery? the scope of trafficking in persons in Africa. Afr Secur Rev 12(1):81–89
Freeman LC (1978) Centrality in social networks conceptual clarification. Soc Networks 1:215–239
Friesendorf C (2007) Pathologies of security governance: efforts against human trafficking in Europe. Secur Dialogue 38(3):379–402
Friesendorf C (2009) Introduction. In: Friesendorf C (ed) Strategies against human trafficking: the rule of the security sector. National Defence Academy and Austrian Ministry of Defence and Sports, Vienna
Germano G (2001) Human trafficking as a transnational problem: the response of destination country. In: Fagbonhungbe T (ed) The rape of the innocent: evolving an initiative against human trafficking, Proceedings of the first Pan-African Conference on Human Trafficking, Abuja (Nigeria), February 19–23 2001
Giménez-Salinas Framis A (2011) Illegal networks or criminal organizations: power, roles and facilitators in four cocaine trafficking structures. Paper presented at the Third Annual Illicit Networks Workshop, Montreal, October 3–4 2011. Retrievable at: http://www.erdr.org/textes/gimenez_salinas-framis.pdf
Hanneman RA, Riddle M (2005) Introduction to social network analysis, University of California, Riverside, published in digital form at http://www.faculty.ucr.edu/~hanneman/nettext/
Hanneman RA, Riddle M (2011) Concepts and measures for basic network analysis. In: Scott J, Carrington PJ (eds) The SAGE Handbook of social network analysis. SAGE Publications, London
IOM (2005) Data and research on human trafficking: a global survey, International Organisation for Migration, Geneva. Retrievable at: http://www.iom.int/jahia/webdav/site/myjahiasite/shared/shared/mainsite/published_docs/books/data_res_human.pdf
Mclllwain J (1999) Organized crime: a social network approach. Crime Law Soc Chang 32(4):301–323
Ministry of the Interior (2007) Rapporto sulla criminalità in Italia, Analisi, prevenzione, contrasto, Roma, 18 giugno
Morselli C (2005) Contacts, opportunities, and criminal enterprise. University of Toronto Press, Toronto
Morselli C (2009a) Hells angels in springtime. Trends Organ Crim 12:145–158
Morselli C (2009b) Inside criminal networks. Springer, New York
Morselli C (2010) Assessing vulnerable and strategic positions in a criminal network. J Contemp Crim Just 26(4):382–392
Morselli C, Giguere C (2006) Legitimate strengths in criminal networks. Crime Law Soc Chang 43(3):185–200
Morselli C, Petit K (2007) Law-enforcement disruption of a drug importation network. Glob Crime 8(2):109–130
Morselli C, Roy J (2008) Brokerage qualifications in ringing operations. Criminology 46(1):71–98
Morselli C, Giguere C, Petit K (2007) The efficiency/security trade-off in criminal networks. Soc Networks 29(1):143–153
Natarajan M (2000) Understanding the structure of a drug trafficking organization: a conversational analysis. In: Natarajan M, Hough M (eds) Illegal drug markets: from research to prevention policy, crime prevention studies. Criminal Justice Press/Willow Tree Press, Monsey
Natarajan M (2006) Understanding the structure of a large heroin distribution network: a quantitative analysis of qualitative data. J Quant Criminol 22(2):171–192
Okojie CEE (2009) International trafficking of women for the purpose of sexual exploitation and prostitution the Nigerian case. Pak J Women’s Stud 16(1–2):147–178
Okojie CEE, Okojie O, Eghafona K, Vincent-Osaghae G, Kalu V (2003) Trafficking of Nigerian girls to Italy. Report of field survey in Edo State, Nigeria, United Nations Interregional Crime and Justice Research Institute, Turin. Retrievable at: http://www.unicri.it/wwd/trafficking/nigeria/docs/rr_okojie_eng.pdf
Oude Breuil BC, Siegel D, van Reenen P, Beijer A, Roos L (2011) Human trafficking revisited: legal, enforcement and ethnographic narratives on sex trafficking to Western Europe. Trends Organ Crim 14:30–46
Petrunov G (2011) Managing money acquired from human trafficking: case study of sex trafficking from Bulgaria to Western Europe. Trends Organ Crim 14(2–3):165–183
Picarelli J (2009) Human trafficking and organized crime in the US & Western Europe. In: Friesendorf C (ed) Strategies against human trafficking: the rule of the security sector. National Defence Academy and Austrian Ministry of Defence and Sports, Vienna
Prina F (2003) Trafficking of Nigerian girls to Italy. Trade and exploitation of minors and young Nigerian women for prostitution in Italy, Research Report July 2003. Retrievable at: http://www.cooperazioneallosviluppo.esteri.it/pdgcs/italiano/speciali/SpecialeNuovo/Pdf/trafficoNigeriane.pdf
Radil SM, Flint C, Tita G (2010) Spatializing social networks: using social network analysis to investigate geographies of gangs rivalry, territoriality, and violence in Los Angeles. Ann Assoc Am Geogr 100(2):307–326
Salt NM (2000) Trafficking and human smuggling: a European prospective. Int Migr 38(3):31–56
Savona EU, Di Nicola A, Decarli S (2002) Mon-Eu-Traf—a pilot study on the three European Union key immigration points for monitoring the trafficking of human beings for the purpose of sexual exploitation across European Union. Report prepared for the European Commission. Retrievable at: http://transcrime.cs.unitn.it/tc/fso/pubblicazioni/TR/03_MON-EU-TRAF.pdf
Savona EU, Belli R, Curtol F, Decarli S, Di Nicola A (2003) Trafficking in persons and smuggling of migrants into Italy (English version). Report realized in collaboration with Direzione Nazionale Antimafia for the Italian Ministry of Justice and the Italian Ministry for Equal Opportunities. Retrievable at: http://transcrime.cs.unitn.it/tc/fso/pubblicazioni/TR/08_Trafficking_and_Smuggling.pdf
Schloenhardt A (1999) Organized crime and the business of migrant trafficking. An economic analysis. Paper presented at the AIC Occasional Seminar, Canberra, November 10 1999. Retrievable at: http://www.cestim.it/argomenti/30traffico/30traffico_economia.pdf
Schwartz DM, Rouselle T (2009) Using social network analysis to target criminal networks. Trends Organ Crim 12:188–207
Scott J (2000) Social network analysis. A handbook, 2nd edn. SAGE Publications, London, Newbury Park and New Delhi
Shelley L (2010) Human trafficking. A global perspective. Cambridge University Press, New York
Siegel D, De Blank S (2010) Women who traffic women: the role of women in human trafficking networks–Dutch cases. Glob Crime 11(4):436–447
Sparrow MK (1991a) Network vulnerabilities and strategic intelligence in law enforcement. Int J Intell Count Intell 5(3):255–274
Sparrow MK (1991b) The application of network analysis to criminal intelligence: an assessment of the prospects. Soc Networks 13(3):251–274
UNESCO (2006) Human trafficking in Nigeria: root causes and recommendations, SHS/CCT/2006/P1/H/2, Policy Paper Poverty Series No. 14, 2 (E), Paris. Retrievable at: http://unesdoc.unesco.org/images/0014/001478/147844e.pdf
UNICEF, UNOHCHR and OSCE (2002) Trafficking in human beings in South Eastern Europe, United Nations Development Programme. Retrievable at: http://www.unicef.org/ceecis/Trafficking.Report.2005.pdf
UNICRI (2005) Programme of action against trafficking in minors and young women from Nigeria into Italy for the purpose of sexual exploitation, United Nations Interregional Crime and Justice Research Institute, Turin. Retrievable at: http://www.cooperazioneallosviluppo.esteri.it/pdgcs/italiano/speciali/SpecialeNuovo/Pdf/programmaUnicriItalia.pdf
UNODC (2009a) Global report on trafficking in persons. United Nations Office on Drugs and Crime, Vienna
UNODC (2009b) Transnational trafficking and the role of law in West Africa. A threat assessment. United Nations Office on Drugs and Crime, Vienna
UNODC (2010) The globalization of crime. A transnational organized crime threat assessment. United Nations Office on Drugs and Crime, Vienna
UNODC/UNICRI (2003) Programme of action against trafficking in minors and young women from Nigeria into Italy for the purpose of sexual exploitation. Report of Field Survey in Edo State
US Department of State (2005) Trafficking in persons report. Department of State, New York
US Department of State (2007) Health consequences of trafficking in persons, United States Department of State–Bureau of Public Affairs, August 8 2007
van der Hulst RC (2008) Introduction to social network analysis (SNA) as an investigative tool. Trends Organ Crim 12:101–121
van der Hulst RC (2011) Terrorist networks: the threat of connectivity. In: Scott J, Carrington PJ (eds) The SAGE handbook of social network analysis. SAGE Publications, Thousand Oaks
van Dijk R (2001) ‘Voodoo’ on the doorstep young Nigerian prostitutes and magic policing in the Netherlands. Africa 71(4):558–586
van Liemt G (2004) Human trafficking in Europe: an economic perspective, Working paper, International Labour Organization, Geneva. Retrievable at: http://www.ilo.org/wcmsp5/groups/public/---ed_norm/---declaration/documents/publication/wcms_081992.pdf
van Moppes D (2006) The African migration movement: routes to Europe, Working paper Migration and Development Series, Report No. 5, Radboud University, Nijmegen. Retrievable at: http://socgeo.ruhosting.nl/html/files/migration/migration5.pdf
Varese F (2006) The structure of a criminal network examined: the Russian Mafia in Rome, Oxford Legal Studies Research Paper No. 21/2006
Väyrynen R (2003) Illegal migration, human trafficking and organized crime. Discussion paper No. 2003/72 presented at the UNU/WIDER Development Conference on poverty, international migration and asylum, Helsinki, September 27–28 2003. Retrievable at: http://www.wider.unu.edu/publications/working-papers/discussion-papers/2003/en_GB/dp2003-072/_files/78091733799863273/default/dp2003-072.pdf
Vermeulen G, van Damme Y, De Bondt W (2010) Perceived involvement of “organised crime” in human trafficking and smuggling. Int Rev Penal Law 81(1–2):247–273
von Lampe K (2003) Criminally exploitable ties: a network approach to organized crime. In: Viano EC, Magallanes J, Bridel L (eds) Transnational organized crime. Myth, power, and profit. Carolina Academic Press, Durham
von Lampe K (2009) Human capital and social capital in criminal networks: introduction to the special issue on the 7th Blankensee Colloquium. Trends Organ Crim 12(2):93–100
Zhang SX (2009) Beyond the ‘Natasha’ story—a review and critique of current research on sex trafficking. Glob Crime 10(3):178–195
Zimmerman C (2003) The health risks and consequences of trafficking in women and adolescents, London School of Hygiene and Tropical Medicine, London. Retrievable at: http://www.Ishtm.ac.uk/hpu/docs/traffickingfinal.pdf
Author information
Authors and Affiliations
Corresponding author
Annex
Annex
Rights and permissions
About this article
Cite this article
Mancuso, M. Not all madams have a central role: analysis of a Nigerian sex trafficking network. Trends Organ Crim 17, 66–88 (2014). https://doi.org/10.1007/s12117-013-9199-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12117-013-9199-z