Latest LinkedIn phishing scam asks users for their personal data to carry further attack through identity theft.
LinkedIn has been in the news for all the bad reasons. Previously, it was the data of 117 million of its users stolen back in 2012, leaked in 2016 and sold on the darknet afterwords. Although, the alleged culprit behind the whole scheme was recently arrested there are people who are still looking ways to steal personal data of LinkedIn users.
In the latest, cyber criminals are targeting LinkedIn users with a sophisticated phishing scam in which the idea is to trick the user into believing that their LinkedIn account has a security issue which can be solved only by providing their personal details.
The campaign was identified by researchers at Heimdal Security who pointed out that the brain behind this scam is looking for users’ financial details, driving license and or passport copy. The purpose of collecting this information is to not only hijacking their account but also conduct further scams by stealing their identity.
The email that is targeting users comes from postmaster fnotify com which is not linked with LinkedIn whatsoever however further research reveals that the email domain associated with the email is actually a WordPress blog registered to a guy Torgeir Salvesen from Finland and seems to be compromised by people behind this scam.
Furthermore, the email content also contains two links. One is a Dropbox link and other is what researchers have identified as a password reset link which leads users to the original LinkedIn password reset page. Apparently, the reason behind this is to trick users into believing that the email is legitimate and their account is in danger for real.
The Dropbox link, however, asks users to upload their viewable scanned copy of the payment method, account holder’s government-issued photo identification, such as a driver’s license or passport and a payment receipt. Remember, asking for payment receipt means the scammers are directly targeting Premium LinkedIn users.
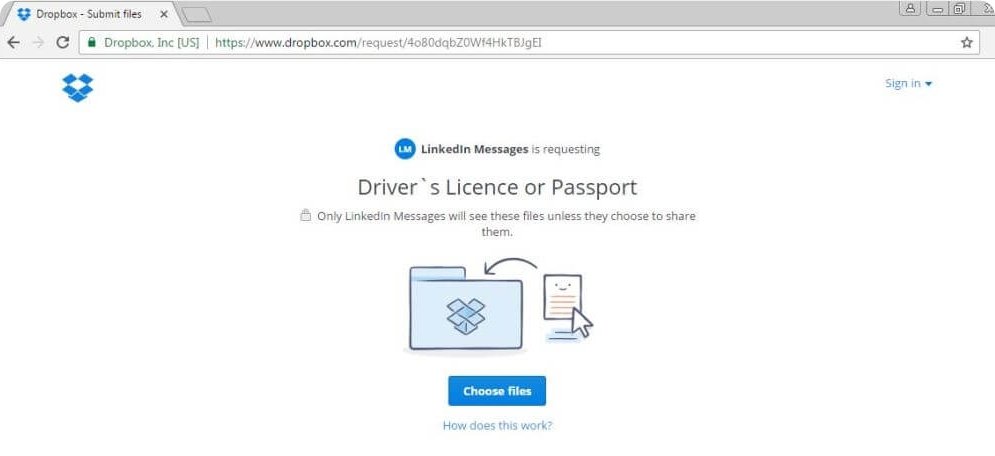
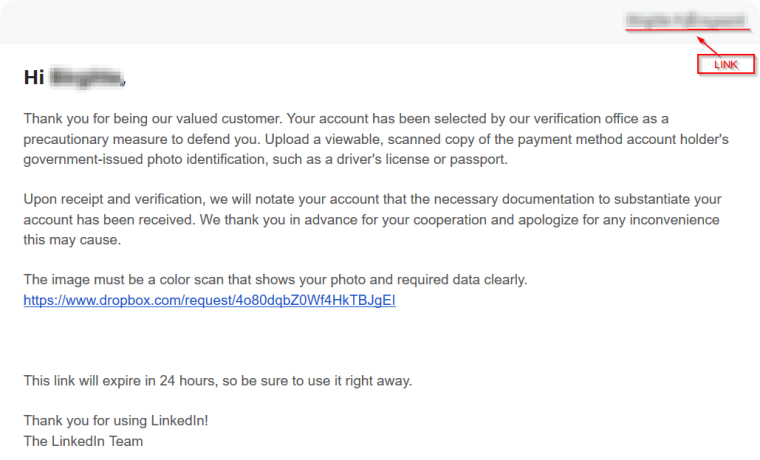
The screenshot below shows a complete preview of the phishing email sent to users. The password reset link which has been censored by the researchers is actually LinkedIn’s password reset link that asks users to change their password to avoid it from being misused. At the same time, there have been a lot of errors from the cyber criminals and looks like they forgot to link the real phishing link on password reset anchor text.
This is not the first time when LinkedIn users have been targeted with such a scam. In the past, the users have been under target by Blackhole malware, trojans developed to steal login credentials of job seekers and even fake profiles pretending as job recruitment officials. All so they can steal personal details of users and use it for identity theft-related scams.
If you are a LinkedIn user watch out for this ongoing scam and click here to visit Heimdal Security’s blog for more technical details.
