Who Hacked The NSA?
The mystery behind the identity of the Shadow Brokers, an eight-foot-tall alien, and the diplomatic chess game surrounding a 234 MB leak

Last week, a group called the “Shadow Brokers” stole 234 megabytes of data from the National Security Agency (NSA). The leak included information about the “cyberweapons” the NSA uses to hack suspects and enemies, and a tracking code that reveals the fingerprints of the NSA’s malicious software.
But, before we can understand the significance of the leak, the mystery behind the identity of the Shadow Brokers, an eight-foot-tall alien, and the diplomatic chess game surrounding it all, we have to start with a report released in 2015.
Last year, the cybersecurity research organization Kaspersky Lab cataloged the most advanced and far-reaching hacking operation ever exposed. The perpetrators, known as the Equation Group, had established hundreds of backdoors in the governments of Russia, China, India, Iraq, and Iran, Britain, Mexico, and France. Forty-two countries in all had been penetrated. The Equation Group had had a penchant for physical attacks, too, intercepting shipments of hardware by IT companies like Fortinet, TopSec, Cisco, and Juniper, whose technologies form the backbone of much of the globe’s cybersecurity infrastructure.

By the time Kapersky pegged the Equation Group as a branch of the NSA’s preemptive hacking task force, TAO, the Equation Group had stealthily compiled an extensive network of backdoors into much of the world’s cyberinfrastructure over the course of 14 years. As an anonymous former TAO member put it for the Washington Post, their files are “the keys to the kingdom.” The files were often organized with weird naming conventions like EPIC BANANA, BANANAGLEE, and EXTRA BACON.
And it’s those files which are being leaked by the Shadow Brokers. Cross-referencing past exploits and code in those files, as well as their unusual naming conventions, against Snowden’s cache and the Equation Group exposé, it’s clear that much of the Brokers’ information comes courtesy of the Equation Group and TAO.
Who did it?
The name “Shadow Brokers” would seem to have been taken most immediately from Mass Effect 2. Yes, the video game. In it, an 8-foot-tall alien called the shadow broker dealt black-market information quietly, and with ruthless calculus–a funny contrast to the hacker group’s behavior.
When the hackers released their cache, they were brazen and braggadocious. Through broken English, they boasted about besting the NSA, and proposed to auction off encrypted NSA data. But the “truly absurd ‘Dr. Evil’ sum” of a million Bitcoins ($576 million) and the fact that losing bidders would forfeit their money without receiving the decryption key indicate the Shadow Brokers don’t seriously expect anything to come from it.
That is, unless it’s an attempt to deflect attention by spurring a wild goose chase for a faux infamy-seeking collective. Much like the character in the game, the broker might be a single individual with access to a vast network, an NSA insider looking to cover his tracks.

Sensitive NSA information is usually stored on air-gapped networks–networks not connected to the Internet. Thanks to that and other security measures, they’re a pain to crack. Humans, however, are easy access points, and as Edward Snowden proved, someone with inside access and a flash drive can bypass such systems.
It’s feasible that the perpetrator is a disgruntled insider trying to deflect attention with a wild goose chase–but going by coincidences, conventional logic, and diplomacy 101, an attack by Russian hackers looks more likely.
Air-gapped networks are good, but not impenetrable. Infect a worker’s phone with malware and you can use it as a conduit to siphon data off an air-gapped network. Infect computers with programs that fluctuate the speed of internal fans, and you can effectively Morse code signal data to a listening device, then code it back into useful information. Such measures might be unnecessary, though, if a TAO operative slipped up and saved sensitive information on an Internet-accessible staging server.
As shown by the recent Democratic National Convention leak by hacker Guccifer 2.0, hackers often claim individual responsibility for attacks. However, it’s generally accepted that such incidents are often state-sponsored, with governments maintaining complete deniability. Russia denied responsibility for the DNC attack, but the White House considered enacting sanctions in response.
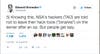
Going with the logic that it was a Russian attack, then this is some excellent diplomacy. In retaliation to the proposal of sanctions, this leak embarrasses the NSA, exposes their backdoors into more Cisco and Fortinet infrastructure, and says, as Snowden puts it:
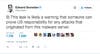
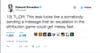
In other words, “back off, because we can show where your fingerprints have been.” And with many of the files dating back to 2013, the Shadow Brokers have been sitting on those fingerprints for some time.
So, the NSA could be dealing with a rogue insider bold enough to not run, instead setting up a wild goose chase impeccably timed to match diplomatic tensions, or a well-oiled and slyly suggestive state-sponsored attack. For now, only one thing is certain: the Shadow Brokers, whoever he, she, or they are, played way too much Mass Effect.