Does anyone else get the feeling that the frequency of rather horrible vulnerabilities coming to light is accelerating? Off the top of our head, there’s Heartbleed, Shellshock, and now this one. The BadUSB exploit attack stems from the “invisible” microcontroller in most USB devices.
We first heard about it when we were attending DEFCON in August. The exploit had been announced the same week at Blackhat but there wasn’t much information out yet. Now the talk has been posted and there’s a well-explained overview article at Big Mess o’ Wires.
Here’s how this one goes: all USB devices rely on a microcontroller to handle the peripheral-side of USB communications. The computer doesn’t care which microcontroller, nor does it have a way of knowing even if it wanted to. The uC is “invisible” in this situation, it’s the interface and data flowing through it that the computer cares about. BadUSB is an attack that adds malicious functionality to this microcontroller. To the computer it’s a perfectly normal and functional USB device, while all the bad stuff is happening on the peripheral’s controller where the computer can’t see it.
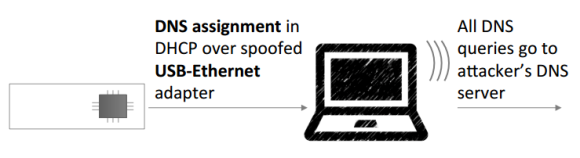
How deeply do you think about plugging each and every USB device? Check out what happens at 19:20 into the video below. The USB device enumerates and very quickly sets up a spoofed Ethernet connection. You can still load a webpage via WiFi but the fake connection is forwarding packets to a second server.
Once discovered, you can wipe the computer and this will stop happening; until you plug the same device again and reinfect. Worse yet, because the controller is invisible to the computer there’s almost no way to scan for infected devices. If you are smart enough to suspect BadUSB, how long will it take you to figure out if its your mouse, your keyboard, a thumb drive, a webcam, your scanner… you get the point.
[Thanks Kuldeep]

















Wait, BadUSB must have a detectable footprint. Why can’t it be intercepted & blocked before it accomplishes anything?
there is no handshake with usb devices – your computer cant tell if plugged keyboard is the same one that was plugged yesterday, it also cant tell if isight camera build into the laptop has the same firmware it had yesterday
https://www.usenix.org/system/files/conference/usenixsecurity14/sec14-paper-brocker.pdf
there is a need for a new firewall in every OS, USB firewall :o
> your computer cant tell if plugged keyboard is the same one that was plugged yesterday, it also cant tell if isight camera build into the laptop has the same firmware it had yesterday
Totally wrong. Each device got vendor and model ID as well as individual number and serial number. OF course that can be spoofed by microcontroller (as they are written in its ROM) and some vendor ignore necessity to setup serial and ID (which creates problem with several similar devices, especially with touchscreens)
As well as action described above is possible only under admin rights, or at least under user which got rights to install devices and driver – microcontroller uses standard stack to tell OS to virtual create device node, or, even more, it may emulate CR and “autorun” own driver from itself. ALL those actions leave footprint.
That’s why having autorun enabled at all times is bad – not only because of infected flash drives, any USB device can do that.
This activity is platform-specific… most likely wont work on Linux,unless Linux got udev and upstart rules for automatically install new Ethernet interface and route traffic to it – windows makes most of it automatically and almost silently. Almost, because since Vista there is device installation pop-up in tray
How is that totally wrong then, you can’t tell if its the same one plugged in, since you can clone it, or its not implemented or as is very often the case the serial number is the same for all of the units,
This is most definitely not platform specific. The USB device isn’t executing code directly, it’s simulating another device to deliver a payload.
On windows it’s easier, but for linux, you could spoof a keyboard and then run terminal commands or take advantage of a bug in a kernel driver for a particular type of device.
How hard do you think it is to find a buffer overflow in a badly supported kernel driver?
Why couldn’t you just disable USB ethernet devices? — I mean there is clearly a detectable footprint when the computer knows what’s plugged in to it — if it says that there is a keyboard, a mouse, and three ethernet adapters all plugged in to USB — that’s a fucking footprint!
The OS could easily show you these things when you plugged a new USB device in that it hasn’t encountered before and confirm with you that you want to allow it.
Even on a compromised mouse, it will show up as at least two devices — a HID device, and some other device — the HID device can be allowed in — and the other device can be gated — and only enablable by some sort of prompt — if that prompt requires the user to type a random number or pass a captcha, etc, then even hijacking the HID-get-sin-free entrypoint becomes impossible.
Problem solved. Someone go code this shit.
“Go code this shit” is the problem. Windows is the problem. They’ve got huge departments dedicated to making things “easier” by hiding all the details and actually making it harder. The default behaviour of disabling file extensions is entirely responsible for trojan.jpg.exe and the like.
But as far as doing shit properly, they’re miles behind, and security is something you add on top, from another vendor.
Simply put, because while the computer can scan the media on a drive, it can’t scan the microcontroller controlling communications to the media. Kind of like the “Can’t see the forest for the trees” metaphor.
And even if it could scan the microcontroller for footprints there wouldn’t be anything malicious to detect. A BadUSB pretending to be a keyboard and executing malicious code would look the same to a computer as a person with a real keyboard executing malicious code.
Not in this situation. That keyboard is showing up as a USB soft hub with two devices connected to it. A HID device, and an ethernet device. — Both of them show up as regular functioning devices. But the keyboard device (other than type keys) shouldn’t be able to do anything malicious on its own.
I didn’t see this mentioned.
http://lifehacker.com/how-to-boost-your-internet-security-with-dnscrypt-510386189
because why not?
OpenVPN can be configured to tell the client to route all traffic including DNS through the server.
DHCP DNS server assignment is on a per-interface basis. This is not a problem.
It is if your computer, like many, is set up to auto-connect to what looks like an ethernet connection when presented in preference to wifi.
Having local network access opens up a variety of exploits that are usually not available.
Granted, if you have a decent firewall, and you keep your security up to date, you should still be fine.
Well you can’t scan for a compromised wifi router, and IMHO they’re easier to hack.
If you’re concerned about NSA backdoors in your equipment, then buy it direct from China so only the Chinese can snoop on you. :-)
Oh wow this was new when USB was released.
No kidding. I’ve seen “hacks” even on HaD about doing almost the exact same thing. I have no idea how this is supposed to be news at a major hacking conference.
I do remember hacks that exploited the Windows ‘AutoRun’ feature from a USB drive but that was only software in static files and not involving the micro-controller to interactively spoof DHCP/DNS.
The previous articles that you are referring to were all using custom hardware or usb dev kits.
The news is that it’s possible to easily modify the firmware in off-the-shelf usb devices to not only provide the normal function but also spoof other devices to deliver a timed payload.
How do you verify that the firmware on the device you own/were given is clean?
The most common usb devices shouldn’t be ASIC or state machines?
How common are reprogrammable microcontrollers in usb devices?
Not sure what you point are.
Because of the complexity of USB protocols, it is unlikely you would implement one using a state machine. A $1 microcontroller can be a USB device.
For the second part, you are asking the wrong question. There aren’t any way you can tell the difference between a preprogrammed microcontroller acting as a USB device and one that’s a state machine. So whether or not common USB devices are state machines have no bearing when you plug in the bad one.
FYI: ASIC = Application Specific Integrated Circuit. It doesn’t say anything about what’s inside just that someone went the trouble of making a chip for a particular application. You can always have a programmable microcontroller inside.
it would be extremely rare to find a usb device which uses an asic instead of a microcontroller for communication. However, for many the firmware is stored in a mask rom and cannot be rewritten thus not susceptible to badusb. Only the first few thousand in production of a common device might use flash rom so that changes to the firmware could be made mid production, but once the firmware is proven a mask rom is often used.
They are only not susceptible in a way you can’t reprogram the original controller. But can you check if the controller wasn’t replaced with different silicon?
The whole point of the scare around badusb is the fact that a computer with a virus could program usb devices plugged into with the modified firmware as a means of spreading itself. If someone you don’t trust has physical access to your device such that they could replace the silicon, badusb is a moot point given that even if the vulnerability didn’t exist they could still modify the device.
Don’t forget about the DFU (device firmware update) function. Many of the projects that I’ve worked on used this facility for manufacturing test, initial firmware load on the line, and firmware updates in the field.. You might or might not be surprised how many chips in current computers and mobile devices use this. While it might seem that initial runs would be flash, then converting to metal mask roms, in my experience is not the usual case. While it would take a fair amount of reverse engineering (or a rogue engineer) to understand the particulars of the targeted device, a determined bad actor could use this attack vector.
95-99% are reprogrammable
exceptions are simple usb-serial bridges, or devices based on Cypress FX2 (downloads firmware on the fly when plugged)
A lot of very cheap USB device controllers are OTP.
None of this matters anyway because the host stack can’t tell if a malicious device is spoofing a safe device.
The answer is extremely common. Practically any USB device that supports OTG functionality (host or slave) has a microcontroller on the port. It’s also cheaper to have your device run the logic it uses on the same mcu it’s using for whatever it does, as long as it can keep up. Two chips are generally more expensive than one chip, as long as that one isn’t significantly more expensive.
How is this any different to an undetected “bad” driver on the system itself? Lots of malware disguises itself quite effectively, and is difficult to detect. Surely, both of these attacks can be detected by looking at the effects they cause (via packet logging)?
Win7 x64 drivers needed to be signed by MS. (That’s a good reason of not defeating the driver signing.) Unlikely you can sneak a bad driver without the user noticing.
You (among many others) aren’t getting it. This can reprogram the firmware on the USB hub in your computer, with code that then reinfects any USB peripheral with a programmable microcontroller attached to that hub afterwards. from there you can listen to data or inject your own data into any stream in either direction.
to clarify – at no point does the operating system know about the modifications. formatting the PC won’t help. switching to linux won’t help.
No, it can’t, unless your USB hub supports firmware updates from attached USB devices. I’d be astonished if there’s any such USB hub out there.
Almost every modern mobo on the planet will accept firmware updates from a USB device.
I feel like we’re talking about different things here. Yes, the motherboard might support going into a firmware update mode and reading the new firmware from a USB stick. That’s entirely different from any arbitrary USB device being able to reprogram the motherboard’s USB hub just by being plugged in.
Ok.
You plug in a usb device.
8 hours later, this device switches to USB hub mode and spoofs a keyboard.
It downloads and runs a small script that identifies your motherboard and then updates the usb device with a specific macro that matches your bios.
It then proceeds to reboot your system while identifying as a keyboard and a mass storage device.
It then plays the downloaded macro, which walks through the process of updating your motherboard with a compromised bios/firmware.
Don’t think you are getting it either. I mention the _DIFFERENCE_ between drivers and USB hardware by pointing out that drivers are signed. i.e. harder to fake.
Win 7x 64 drivers need to be signed by an MS certificate, not by MS . Which aren’t that hard to get.I have my own personal cert i can sign x64 drivers with, sure a user could notice that once they know what to look for, but the OS won’t complain about the install.
Also using someone else’s cert is obviously harder, or rather keeping a driver cert sign valid after tamping with the executeable, but that is also doable.
Microsoft is US company and could have a blanket and anonymous back door put in if the relevant spook agency ordered it.
Microsoft, as a matter of fact, DOES have a blanket and anonymous backdoor available for internal/law enforcement use to be able to gain root access to any device in the world that is running Windows and is connected to the internet. The access keys are highly secure and extremely tightly guarded and very few people, even within the company, know of its official existence. The only reason I’m aware of it is because my father, before he retired, used to be one of the two people in the company who knew how to use the backdoor and also had the access keys. Damages resulting from the malicious use of this backdoor could be devastating, and, because it is actually a designed part of the operating system, not one single Windows-based device is invulnerable or can be hardened against it. However, because of the security measures in place regarding it (full access is limited to two people on the planet and immediate and harsh legal action can be taken in the wake of any unauthorized use), it is very unlikely that it would or even could ever be used as any sort of attack vector.
I used too work for a company that made encryption boards for high-end clients, such as the branch banks of the Federal Reserve. That was back in the early 90s, prior to the Digital Telephony Act of 1994 (CALEA) which basically nationalized the Telecommunications industry and was later expanded. Our CEO was approached by the NSA to put a back door in the encryption boards, and since that was back in the day when you could say no without being put out of business, our boss said “no”. So I don’t doubt that the NSA has backdoor access not only into Windows but into IME (Intel Management Engine), but what is not well known is that Israel is the real power behind the throne. But that’s another story. Read Bamford’s The Shadow Factory for more on that.
Perhaps if you mean looking for malicious signatures amongst the activities occurring over the USB bus. These would not be far off from valid activities and would be hard. From what ive seen the devices themselves aren’t abnormal and can function with valid device drivers.
IE: HID device sending keycodes, normal. If the keycodes happen open a run dialog and popup the command prompt, still somewhat normal. However, sending keystrokes at 500 words per second, or dumping 500 bytes of hex into powershell probably not.
But then there are special gaming keyboards that may do more than a normal keyboard does, so this check may make it invalid, or gaming keyboards may appear “malicious”.
Reblogged this on @stevebanfield and commented:
I think we’ve all suspected that malicious peripherals could be a threat but this really makes it clear how much of a threat. As always don’t install anything, software or hardware, unless you are sure you can trust the source.
How is this “news” exactly?
Beware, there are also a lot of other computer stuff that can be hacked like this, for example some RAID cards use some MCU/FPGA that connects to the upstream PCIe port, if you flash another firmware, you can make it act like a video card, or ethernet. Wow!
Excuse me, may I charge the battery on my RAID card by plugging it into your laptop?
I’m a bit confused–previous coverage said that it was a fundamental security flaw in how USB works, but from this article and the linked content it appears to be a flaw in the implementation of USB devices and OS’s (all of which currently automatically trust USB devices that identify themselves as things like keyboards.)
It seems like this attack vector could be dealt with by:
1. Making USB devices that don’t let their controller firmware get upgraded insecurely, and
2. Changing OS’s so that they don’t automatically trust devices (have a confirmation dialog ask “Did you just plug in a keyboard?” to alert the user who just plugged in a thumbstick drive.)
Sounds like a good point … at first. But how to confirm such a question if you just plugged-in your ‘real’ keyboard? :o
Remember: The OS cannot recognize, that you plugged in the same keyboard you used yesterday. Each start-up would be accompanied by confirming like 10 devices (Mouse, Keyboard, Cam, Mic, USB-Sound, USB-Ethernet, SD-Card Reader, AVR-Programmer, Scanner, Printer, USB-2-Serial, USB-Hub, …)
Hmm, but maybe one can define certain USB-Root Hubs as Secure. So one of your System’s USB Controllers (If you have more than one) is something like a demilitarized zone ^^
Make the user solve a captcha everytime a USB device is plugged in ಠ_ಠ
But this isn’t anything new – all you’re saying is that any USB device you plug in could have hidden functionality.
Yeah but we’re all screwed together, if it isnt some obscure firmware in a complex OS it’s a wireless injection or internet code injection or hidden PCB antenna or hidden memory loading before BIOS. No one can stop it all.
What we need is a public fuse-based OTP ROM which would be hard, annoying, low features…but assured non-malicious logic everyone could build on with non paranoid thoughts clouding and ruining our minds…
abacus
Curta?
now that is neat.
Lol neat, but I want electricity though. But visible fuses on the ROM if we’re going to be serious; question tiny cells of ROM and interfacing w/ them may still be a problem (ie the same damn problem of another chip doing it). There’s too much packed in chips these days!
It’s been done in the past though, other types of ROM too (secure, not very useful though…).
Lol, too far back…
*Backhat :D
Thanks, fixed.
I think the talk about this exploit is over-blown. From what I understand it was done one chipset. Many devices cannot be reprogrammed. Otherwise this is a classic man in the middle attack. It is always possible to spoof any verification that your machine requires for something that is connected to it. At some point it is impossible to verify everything short of building your own chip factory and making all the hardware yourself. I guess in theory hackers could start making their own modified hardware just like the NSA did. At that level it means someone is investing a lot of time and effort to get you. It would follow that what you have must be very valuable and at that point a person should spare no expense to verify their stuff. I bet the NSA does.
I agree. [Mike Szczys] and others are talking like this can somehow directly reprogram any MCU in any USB device. It can’t.
It must first load software on the host, with success depending on being able to exploit an unpatched vulnerability that allows it to silently do so. If successful, it can then only reprogram devices containing one specific MCU, with a specific bootloader, that also has the options set to allow updates. Even then there’s a high probability it will either fail, brick the device, or break its original functionality. The latter two events, if it happened to enough people, would lead to discovery of the hostile software and release of antivirus signatures for it; limiting the spread of something that was already very limited in effectiveness.
And for the paranoid who are worried about the “hey, can I charge my phone on your computer” scenario, build yourself a little USB extension cable with the data lines cut, and make them plug it into that instead. Problem solved.
I have a USB cable from a euroshop which doesn’t have the data lines in it, which probably saved a few cents on the cost of production.
While it’s great for security, it sucks for charging my device – it will turn any “fast” charger, or USB “charge port” or “sleep-and-charge port” into a standard usb port with max 500mA, since the data lines carry the signal to the device that this port can do more than 500mA.
Add a resisor on an small extender and your cable is still save and your devices still thinks its connected (please note that each device could need a diferent setup of resistors and/or values. Or and diferent circuit)
If you have an Android device, you only need to tie the data lines to each other on the device side.
How about a AGC type circuit with sensing? It can quickly decrease the resistance till it hits the standard max for the power line then slowly decrease till the voltage rises just slightly.
@Matt Nunez
Agreed. I’ve yet to see a scenario where getting hit by this vulnerability where you don’t have bigger problems. There are really only four possibilities:
1. You used a thumb drive you found on the side of the road. You are an idiot, and no force can protect you from yourself. You’re doomed.
2. Some person or organization has managed to place convincingly legit-looking hardware into some actually legit venue (if you buy hardware from some fly by night street vendor, see #1). This involves building a real supply chain, which requires moving capital around on a scale that is likely to attract Big Deal attention. You are dealing with either a state actor or serious organized crime. You are completely boned.
3. You computer has been remotely compromised to the point where an outside party can install whatever they want. Even before they apply the exploit they already have all of your information. The horse has left the barn through one of the walls, and the closed/open status of the doors is now irrelevant.
4. Someone has physical access to your hardware. They can already fuck with you without this vulnerability, and given that this scenario means you’ve been targeted as an individual, they probably will.
I would agree that this isn’t a big vulnerability. There are at least two layers of security you have to get through to ‘infect’ the OS of the machine with a virus or malware. The OS patch level would have to be out of date *and* your antivirus software has to be out of date *and* even then, you only get the privileges of the logged in user. The only other way to gain elevated privs is with a 0 day exploit of some kind.
It’s been said long before now that if someone has access to the console of the machine, they can do whatever they want with the hardware. I think I read that on usenet sometime around 1995 and no one panicked at the time…
Not sure what the fuss is all about. Generally I’m not that concerned with physical attack vectors, but this is even more underwhelming.
I mean, isn’t it just a question of time before most laptops ship with a thunderbolt/lightning’esq connector? What could possibly go wrong there!?!?!? Exposing the main bus like that…
Or plug your ethernet or wifi into a malevolent socket and there you go as well.
Ports have a certain risk… just as everything else.
Laptops have had pcmcia and expresscard which has always been a direct bus connection.
Those same laptops also had USB. Not sure what you point is here..
Paranoia fuel for people with home made keyboards that use an arduino sketch they downloaded from the internet as their firmware.
What firmwarez do you use pirate?
Not piracy – just homebrew.
Ergodox is a common open source keyboard that people make http://ergodox.org/
The firmware is here: https://github.com/benblazak/ergodox-firmware
The ergodox uses an arduino as its controller, so its easy to update the firmware to do things. I got all exicted about this a ways back and was talking about making a custom keyboard wherein I could make it aware of which application I was using and have different macros for each app. The blackhat in the corner of the room giggled loudly at the other possibilites of such a thing.
If I build a custom keyboard, I’m not going to leave it unattended at my hacker space.
Was referring to your weblink. I don’t get how people can type on that (or start all over and get used to it), but more power to them I guess.
The ergodox.org link now redirects to some spam site selling som eoverpriced “how to make money” shite.. Dont click it
As others have pointed out, this is massively overblown. The broader issue only affects USB devices that support firmware updates over USB – a small minority of devices – and the specific vulnerability is in only one small manufacturer’s devices. Without this vulnerability, it devolves to “someone could give you a malicious USB device”, which ought to be news to exactly nobody.
you misspelled majority
do you have a digital camera? 100% of those are susceptible
do you have a pendrive? 100% of those are susceptible
small? phison is like 30% of the market, other big ine is Alcor – and it has as buggy and open firmware as Phison, you can actually read raw flash pages or change flash controllers configuration (destroying all the data) on the fly with ONE custom scsi command on Alcor flash drives.
> Without this vulnerability, it devolves to “someone could give you a malicious USB device”
with this vuln its “you could put your flash drive in a wrong hole and get infected WITHOUT A TRACE”, Think TSA/Customs plugging every single flash drive/camera they can find in your luggage.
You cant even scan your flash drive to be sure it wasnt infected, we will need custom safe firmware (with disabled upgrading) to be secure.
Even if what you say is right – and I doubt 100% of digital cameras have USB firmware upgradable over USB, and are capable of presenting alternate interfaces – this is an issue with those firmwares and their facility for online upgrades. It’s not a fundamental weakness in USB itself.
I disagree. I think the fundamental weakness is that USB inherently trusts the plugged hardware to be what it says it is. Sure, the majority of the time this is just fine (we hope). But a more desirable feature would be the option to have a handshake or pairing with the device that let’s the OS know it’s the same one (unaltered at the firmware level) that was previously plugged in.
So assuming that the firmware can be compromised on an arbitrary device, what would prevent the malicious device from succeeding with its handshake? Firmware checksum? Lie about it. Return a private key? You could probably learn what it was before you overwrite the device.
Besides, if you overwrite the firmware, wouldn’t it just be seen as a new device anyways? If you’re camera is hacked into being something else, it’ll show up as that something else and do the whole install process again, unless it was hacked into being a malicious camera. But what’s it going to do? Refuse to take your picture?
I’m with some of the others here, I’m not really seeing the issues. Perhaps this article could be rewritten worn some better examples?
@CodeRed
If it shows up as something new to the host, wouldn’t the system flag it as a new install? If you already installed the driver and the next time you plugged it in it shows up as a new device, shouldn’t that tell the user that something is wrong?
I agree it is a design flaw with USB. I think a simple way around the problem would have been to design USB such that each USB port is assigned a physical port address. The first port on the root hub would have address “1”, the second port would have address “2”. if a device is plugged into a hub, the hub address would be added before the port address, EG a device plugged into the second port of a hub which is itself plugged into the first port on the root hub would have the address “1.2”
A decent OS could simply firewall the devices, for example to only accept keyboard entry on port “1.2”, if a keyboard appears on any other port it is either ignored or the user has to login from that keyboard before they are allowed to use it. Drivers could be blocked from accessing USB ports they are not permitted to.
I think you are looking at the wrong side of the problem.
Looks like you (and almost everybody) are thinking about the security of the USB devices, that they can be reprogrammed by an evil agent. This is not the point of the BadUSB presentation.
The real problem is on the host side. If you find a 64GB USB drive “lost” on the parking lot of your company, you will SURELY get it and plug it on your computer to see what it have. The point is that even if you format the drive on a dumb machine, before plugging on your real computer, it can attack you. You can use dd on Linux, started from a live-CD to overwrite the entire disk with zeros, ten times over, and it will attack your computer.
A reprogrammed USB stick can detect what OS is running it, based on the behavior of the bus, and behave accordingly, and add any delay to avoid you blaming the pendrive for any strange message or activity.
Some of the attacks:
– It can create a virtual interface, and change the DNS servers. Instant invisible phishing.
– It can create a virtual keyboard and execute a powershell script, downloading anything it wants, even if your connection uses a proxy. It can use Internet Explorer to download, because the firewall will allow it.
– Even if a USB stick does not have enough processing power, one can create a ARM-based device, put it inside a pendrive, create a virtual monitor and record everything on your screen, save it to a hidden partition, use keyboard emulator to download start a program that detects when you locks the screen, and upload everything you did. It can do all of the above using a “formatted” USB drive.
– It can create a hidden partition, and put attack software there. Adding the ability to detect the OS, and run programs, it can attack any device plugged in, creating or changing files, or copying data to upload later.
And the attacks are almost invisible, and if you see something amiss, you are not likely to blame the formatted pendrive you connected 10 minutes before.
The driver signature does not protect you here. The device can say it is whatever it wants, so absolutely nothing prevents the device telling that it is a genuine Intel USB Network Card, loading Intel drivers, and creating a Intel interface. Or a Microsoft keyboard. Or anything it wants. The driver does not matter, as the faked device will only perform basic functions, so it won’t depend on anything advanced on the driver itself.
The host side is the real problem, not the USB device.
None of the attacks you describe require BadUSB, though, or would be solved if there were no devices that can have firmware reprogrammed over USB. All of these attacks could be achieved by simply creating something that looks like a USB thumbdrive but contains a USB-enabled microcontroller.
No, the BadUSB attack shows that there’s no host-side security on USB. This is the point of the attack. Even if no device could be reprogrammed, the BadUSB would happen, it would only be harder.
Now, creating a firewall for USB devices would be a good measure to preventing this attack. Plugging a USB stick and getting a “New NIC Card” notification would look very suspicious.
No, BadUSB is specifically an attack that involves reprogramming the firmware on an existing USB device.
Bas usb is about the reprogramming of the firmware. Creating a ‘bad’ usb device is easy but it requires an attacker to buy a piece of hardware for each device it wants to attack.
The reprogramming part is the really scary part. If an attacker can reprogram an ordinary device it only has to write a single program and we can never trust any usb device because it can spread.
The upcoming USB spec (when there is going to be one) should include some kind of pairing mechanism like Bluetooth which would involve digitally signed descriptors. With a TOFU policy we could be sure no one has fiddled with our pen drive. However the problem of rouge HID devices possibly sending something like “rm -rf /”.
Why bring RF into this? They spoofed an ethernet connection, think Bluetooth is immune to that?
It’s not about medium. It’s about pairing devices and being sure your pendrive can’t develop an ethernet interfaces in its armpit behind your back. Which is quite easy if the “pendrive” (read: “a device”) is implemented in software on a board with UDC running Linux.
you clearly didnt understand his post
he advocates for per device handshake, explicitly whitelisting trusted devices.
This will only drive up cost for name-brand devices. Cheap $1 USB flash drive manufacturers will find loopholes to avoid the manufacturing costs to uniquely sign each device, and major OSes will allow easy ways to whitelist devices with half-assed authentication to avoid consumer backlash.
i think not true, look at the git were most of the goodies are.
https://github.com/adamcaudill/Psychson
Based on user feedback, the following devices have been found to have a supported controller:
Patriot 8GB Supersonic Xpress
Kingston DataTraveler 3.0 T111 8GB
Silicon power marvel M60 64GB
Toshiba TransMemory-MX™ Black 16 GB
Patriot Stellar 64 Gb Phison
thats high end stuff i think..
it was nice of them to write a full how to tutorial, even on setting up te build enviroment.
It is really just using a “USB Rubber Ducky” for evil. It is not new.
it is new when all of a sudden your trusted pendrive you owned for 3 years starts adding little extra content to every .EXE file you store on it.
It is interesting to note that the SONYDRM rootkit got in through standard CDs and spread globally before anyone even noticed.
Bluray actually includes a “Kill Switch” as part of the standard in the form of the CSS/CPPM system, and people have indeed trashed perfectly good players because they had the misfortune to run into a bad disk combination that borked the firmware.
The only solution is to have a “Secure” port which uses obfuscation of pins ie V+ as Gnd and detects a pilot tone or tones before it enables normal Vcc.
Also using +3.92V in place of +5V would help here as this would fox the most common MITM attacks and allow the same port to charge devices and be used for BT/7.1ch headsets etc without ever compromising security.
Suggest a new standard – USB+S in the form of a 4 pin headphone socket with the above mentioned features allowing a multifunction port to be used.
What the… are you just sprouting random combinations of technical terms?
I think he is trying to say there should be a handshake on the power line. Sadly, that would change fuck all due to how this kind of malware spreads.
On topic:
Why is this a thing again? There was a similar scare back in the 90s about something similar with the parallel port and again in the 00s with serial ports and in the 10s it’s USB giving us grief (for a third time since 2009).
If you handshake on the power lines, you can do away with the data lines! Genius!
Quick, to the patent office & IPO before anyone looks too closely!
USB-over-1Wire. Outstanding.
Maxim, launch the lawyer squad!
yeah and firewire, oh wait.
Obfuscation is NEVER security. In the end the device needs to work or it’s pointless.
Here is an new one for you, you know how you can use an LED as a light, or a sensor, well that means a lot of LEDs on different devices could become covert I/O ports.
I just thought I’d mention this given that they mention in the talk that badUSB can install badBIOS etc. Then data can start leaking out of every switchable component your CPU can toggle fast enough, and that can even includes unused pins via RF if the box has inadequate shielding.
Not so fast cowboy. USB devices, unlike IEEE1394, talk only on hosts’ requests. A USB device can’t force a host to do anything it can only fool it. So if we make sure device drivers don’t do stupid things AND devices we trust don’t change behind our backs we are mostly on the safe side.
Watch the entire video, the problem is that the current spec does not let you prevent things happening behind your back. Going forward it can be fixed if the will is there in the industry, but everything that exists now does have the flaw.
I recall people abusing U3 usb sticks for something like this? in effect killing the whole U3 market? or was that just a case of loading iso’s with malicious code?
U3 was such an abomination Every Sandisk Flashstorage that came with it was immediately wiped from all this. Where there even one person that was excited about U3?
This is why we can’t have nice things.
This runs code directly from codespace of the mcu in the device. This means you can write your own driver for the device and store it in the device . Been doing this for years, it’s ‘new’ because more people are turning over / explaining these xploits to people who have the ability to fix it. I think its going to get harder to sell usb sticks at garage sales . . .
Would’ve gone with ‘We’re all totally and completely Plugged’
DIdn’t give a shit 5 years ago, so I sure don’t now. Slow news week at the cons I guess. I would have to guess there is some sort of declawing method *cough cough* but I did not find the original exploit *cough cough* and only two countries would ever actively try to support its use maliciously and they already have so it is kinda a moot point now. Carry on and keep buying cheap crap and hooking it to your computer. I have more coffee to finish.
What’s not totally clear from this talk (at least from my viewing) is whether a flashdrive can re-program another flashdrive in the field to propagate the virus around between multiple USB devices.
I get the impression you need to wire up some contacts on a USB uC or it’s ROM chip to a chip programmer to rewrite it’s firmware, so if the on-board uC cannot be directly contacted by the host computer, then there’s no chance of propagation of BadUsb other than the software it puts on a PC.
Many flashdrives can be reprogrammed over USB via a program running on the host OS. No need to wire anything.
I once bought a cheap 8GB drive that turned out to be a 1GB drive with it’s controller fraudulently reprogrammed to show 8GB to the OS. By searching on the internet I was able to download a tool from the IC manufacturer to flash the controller and I fixed my drive to a fully functioning 1GB drive. You can find many examples like this on the internet.
I’m pretty sure malware could propagate with this method, the only challenge would be making it compatible with as much flashdrives as possible.
Don’t be so sure – many USB devices have hardcoded device descriptors, even if the firmware is updatable. So you could make firmware that infects any files stored on it, but not firmware that pretends to be a keyboard, for instance.
Shellshock is a scare campaign, bash? really? dont ask if your watch has a bash shell in it, ask what the media is trying to distract you from. ( I really hope nobody is still using bash cgi for anything publically accessable still )
Why bother going to all the work to modify an unknown usb controller firmware when you can add a extension rom to the bios? 98% of all PC’s use the same BIOS extention system. I mean, unless your a malicious organization trying to spy on a forign government or sabotage a forign countrys nuclear weapons refineries….
A nice validation would be to have “device permission”, similar to how Android apps tells what permissions it needs before it can be installed. This could lead to a new kind of drivers, or handshakes between the computer and USB devices.
What we need is a USB condom.
or stop screwing around
I have screwed up a ton of Atmega Chips because the fuses were programmed badly. These can only be resurrected with a much higher voltage, often more than 5 v, and require seperate physical hardware. Maybe there is a fix for some old devices.
I was thinking the same thing or even just make it where you need to jumper two pins to enter programming mode.
Plugging in my USB Popcorn maker.
All you guys are focused on the security issue, and missing a bigger picture. A reprogrammable MCU that comes packaged with gigabytes of Flash and some RAM, for less than ten bucks. Move over, Arduino.
you will like this
https://bitbucket.org/flowswitch/phison
this is the project that was a base for badusb on phison chips
In Linux you may detect if there were any usb device acts as network device, even for a short time, with command:
$ dmesg |grep -i usb |grep -i interface
is this a comedy for microsoft? to authorize him to bring a new user friendly jails and nonstandards ?
what the hell was that, second, guy saying … I couldn’t understand a work he said.
Buy anyway cool idea about usb devices, acting like, literal, trojan horses.
This is a human problem not a technology problem. Hardware manufacturers have leaft their devices wide open when they should have implemented better security. End of story.
you can compare it to shipping EVERY SINGLE piece of networking gear with wide open Telnet running on default port with no password with root privileges – does that sound like human, or technological problem?
Well, you need to put a stranger’s USB stick into your computer, which is not ‘all screwed’, but then there is the businesses and government we rely on, but I would expect by this time after years of USB theft and software issues most important systems have USB ports disabled for access.
So all in all, I think this isn’t so dramatic as ‘we are all screwed’.
1. The hack works only on computers that use wifi. 2.”Add new device” in Windows is in no way fast. It can take a minute or so. 3. It requires you to be a local admin. 4. Your new “hacked” network adapters are entirely visible in all settings. 5. On a laptop, you will suddenly have 2 Ethernet cards, WTF? 6. Your new “hacked / magic” network card disappears when you unplug the “happy found” USB memory. 7. A laptop is square and easy to handle. But not if it has USB devices connected. The USB device will seldom be connected. 8. It is easy to track a suspect USB device if you only HAVE A SINGLE ONE. 9. Windows Firewall will ask if this is a “home network” or “public network” when you have not connected the new LAN hardware. 10. A large majority of countries in the world are dictatorships (China, Russia, Iran, Africa, etc.). The police can beat you over the head with a brick and after 5 cents of electroshock you tell all the passwords you can and then some. Completely legal.
(China, US, UK, Russia, Iran, EU, Africa, etc.)*
Hey, couldn’t we monitor USB traffic and see the DNS queries or other data that doesn’t look normal?
I googled usb sniffing and found a couple programs
http://www.usblyzer.com commerical
and http://sourceforge.net/projects/usbsnoop/ free
Holy balls of fur, just a few days ago I noticed that the backsides of the screens at a local bank are pointed towards the client, and that they have USB ports there. I already thought about how stupid that is, one could plug in a wireless keyboard/mouse, but this is even worse. Damn.
Those ports only work if you connect the monitors to the pc with a USB cable. Cables, though cheap, cost money, so there’s a good chance the ones you saw are not actually connected even if no one there has a clue about security.
May be an all-in-one computer. They are used often at counters, info desks, etc.
Not an all-in-one thing. It’s a plain screen. But I also came to the conclusion that it’s probably not even connected to the computer. Let’s hope so, I have my money at that bank.
OK, TL:DR on the comments (I tried, I really did), so I may be repeating someone else.
My bottom line on this: there are small, inexpensive devices with a programmable chip and beaucoup memory available for cheap. At gas stations, no less.
What can we use this for? Besides what the demo tried to make us afraid of, that is….
Of course doing this exploit would require physical access to the machine.
As far as reprogramming a normal device into a bad USB device that would require both a flash setup to be reprogrammable via the host USB interface vs mask rom or OTP microcontroller and knowledge of the microcontroller used in the device.
Part of the fix would be to have all the fuses in the device set so it cannot be reprogrammed over USB or use a mask rom or OTP device.
If user upgradable flash is a must then design the controller to require a pin to be grounded via jumper for firmware updates.
Link encryption between the device and the driver should ensure that any “piggyback” devices become a garbled mess.
Anything that doesn’t have the right encryption will not kick the driver and should therefore come up as an unidentified device which has its i/o neutered until it’s been identified.
The issue here of course is that this doesn’t do anything for the billions of currently functional usb devices that can’t be configured to offer some kind of secure link technology.
Thunderbolt however…
Grounding a pin is easy to do if you are manufacturing evil chips that are always in program mode. (but that would be discoverable by the OS)