Update: the flaw has been fixed, and Twitter now says it is safe to use twitter.com again.
Sarah Brown is among thousands of Twitter users who have been hit by malicious use of a security flaw in the redesigned Twitter site.
The wife of the former prime minister Gordon Brown, who has more than a million followers on Twitter, unknowingly sent a link which contained malicious code that would redirect anyone who moved their mouse over it - but didn't click it - to a Japanese hard-core pornography site.
The problem only occurs for people who are viewing links on the Twitter website itself. People who use third-party clients, which access the back-end database to the site, are not affected, because the code is disabled by the programs.
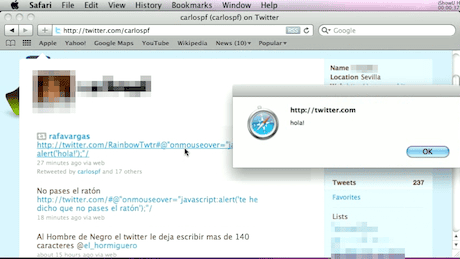
Graham Cluley, security expert at Sophos, warns that "The Twitter website is being widely exploited by users who have stumbled across a flaw which allows messages to pop-up and third-party websites to open in your browser just by moving your mouse over a link.
"Thousands of Twitter accounts have posted messages exploiting the flaw."
The problem arises because users are able to post chunks of Javascript program code inside tweets - and because Twitter has not taking precautions to disable the code by "escaping" the relevant characters, the Javascript becomes active.
The specific code being used is onMouseOver, which carries out a function when you move the mouse over the link. Users don't have to click the link to be redirected.
Some users are using the code to create "rainbow" tweets with blocks of colour.
The exploit, using a method known as "cross-site scripting" (XSS), will be an embarrassment for Twitter, which launched its new-look website a week ago, including links to third-party sites for pictures and video.
Cluley commented: "It looks like many users are currently using the flaw for fun and games, but there is obviously the potential for cybercriminals to redirect users to third-party websites containing malicious code, or for spam advertising pop-ups to be displayed.
"Hopefully Twitter will shut down this loophole as soon as possible - disallowing users to post the onMouseOver JavaScript code, and protecting users whose browsing may be at risk."


Comments (…)
Sign in or create your Guardian account to join the discussion