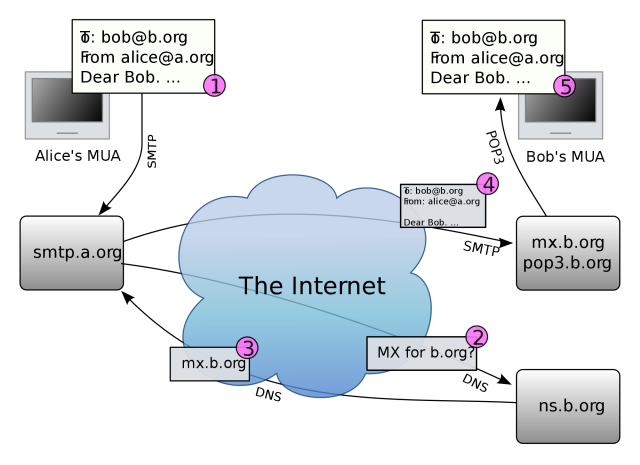
Researchers have some good and bad news about the availability of secure e-mail. Use of STARTTLS and three other security extensions has surged in recent months, but their failure rate remains high, in large part because of active attacks that downgrade encrypted connections to unencrypted ones.
That conclusion, reached in a recently published research paper, means that a significant chunk of e-mail continues to be transmitted in plaintext and with no mechanism for verifying that a message hasn't been tampered with while it travels from sender to receiver. The downgrades are largely made possible by the simple mail transfer protocol used by many e-mail services. Because it wasn't originally designed to provide message confidentiality or integrity, it relies on later-developed extensions including STARTTLS, domainkeys Identified Mail, sender policy framework, and domain-based message authentication that often don't work as intended.
The researchers wrote:
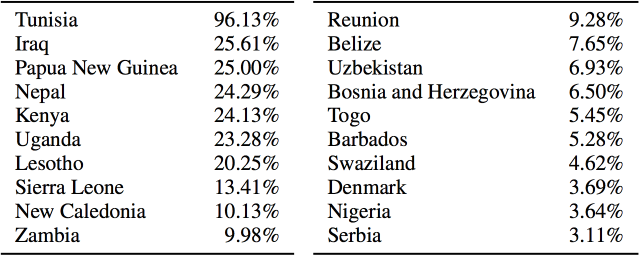
This security patchwork—paired with opportunistic encryption that favors failing open and transmitting messages in cleartext, so as to allow incremental adoption—enables network attackers to intercept and surveil mail. In one such attack, network appliances corrupt STARTTLS connection attempts and downgrade messages to non-encrypted channels. We identify 41,405 SMTP servers in 4,714 ASes and 193 countries that cannot protect mail from passive eavesdroppers due to STARTTLS corruption on the network. We analyze the mail sent to Gmail from these hosts and find that in seven countries, more than 20% of all messages are actively prevented from being encrypted. In the most severe case, 96% of messages sent from Tunisia to Gmail are downgraded to cleartext.
The findings are based on Gmail SMTP connection logs spanning from January 2014 to April 2015 and a snapshot of SMTP server configurations from April 2015 from the Alexa top million domains. The Gmail data showed that incoming messages protected by transport layer security encryption grew 82 percent in one year, peaking to 60 percent of all inbound mail by the end of the study. Outgoing messages increased 54 percent, with 80 percent of messages protected. The improvement was largely the result of Yahoo, Outlook, and a small number of other large e-mail providers updating their servers to use STARTTLS.
Offsetting that progress was a finding that about 770,000 SMTP servers associated with the Alexa top million list still failed to properly secure their systems. Only 82 percent of them supported TLS, and of those, only 35 percent were properly configured to allow one server to cryptographically authenticate itself to another.
STARTTLS corruption
The researchers also found evidence of widespread corruption that prevents STARTTLS from working as intended. Like many security mechanisms, STARTTLS is designed to "fail open" rather than "fail closed," meaning that when certain errors happen, servers will simply send e-mail in unencrypted form rather than failing to send the message at all. Network actors can exploit this design by sending certain types of packets that trigger a fail open error. The overall fraction of Gmail messages that were downgraded was relatively small, but in Tunisia, TLS was stripped out of 96 percent of e-mail. Other countries with high rates included Iraq, Papua New Guinea, and Nepal.
"It is important to note that the devices that are stripping TLS from SMTP connections are not inherently malicious, and many of these devices may be deployed to facilitation legitimate filtering," the paper states. "Regardless of intent, this technique results in messages being sent in cleartext over the public Internet, enabling passive eavesdropping and other attacks."
The findings suggest that even as e-mail providers continue to deploy STARTTLS, there's no guarantee that e-mail will be encrypted as it travels from one server to another on its way to the receiver. That leaves the truly paranoid with no other option than GPG or MIME to ensure the confidentiality of the messages they send.
reader comments
95