
Two days ago, Ars ran a syndicated story by software developer Naoki Hiroshima on how his potentially valuable Twitter handle was stolen (the story originally appeared on Medium). Hiroshima described a painful ordeal wherein an attacker extracted credit card information from his PayPal account, used that information to reset the login credentials for Hiroshima's GoDaddy account, and then modified the domain's MX records (the set of DNS entries that tell everyone else on the Internet where to send that domain's e-mail) away from Hiroshima's servers to their own. The attacker also appeared to have modified a number of other details of Hiroshima's GoDaddy account, making it impossible for Hiroshima to gain access. The attacker then attempted to reset the password to Hiroshima's Twitter account, "@N," but was unsuccessful.
Unable to gain access to the @N account, the attacker then e-mailed Hiroshima and threatened to take action against Hiroshima's website's domains unless he changed his Twitter handle to something else, allowing the attacker to assume the "@N" handle—which he would then presumably sell.
Hiroshima attempted to regain access to his GoDaddy account, but GoDaddy wouldn't restore his access, because Hiroshima no longer appeared to be the legitimate owner of the account. Even involving a GoDaddy executive didn't appear to fix things. A day later, after further threats from the attacker, Hiroshima surrendered the @N handle, and the attacker promptly sent Hiroshima his GoDaddy login credentials. It was a successful hostage exchange, as such things go, but Hiroshima found himself victimized with no apparent recourse other than acceding to the attacker's demands.
The actual "exchange" didn't involve exchanging anything—Hiroshima changed the handle on his Twitter account to "@N_is_stolen", which allowed the attacker to change the handle on his own account from whatever it was previously to "@N." Hiroshima retained his tweets, his friends list, and all the other account properties.
After gaining control of the @N name, the attacker turned downright magnanimous, describing what he allegedly did at each step of the process. From PayPal, the attacker said he acquired the last four digits of Hiroshima's credit card. Those four digits were enough proof for GoDaddy customer service to allegedly let the attacker repeatedly guess at two more credit card numbers, which won the attacker a password reset on the GoDaddy account. From Twitter's perspective, nothing illicit had taken place—just a few accounts changing their handles.
PayPal’s response
Naturally, Hiroshima's tale gained a lot of attention. The first company to make a statement was PayPal, which released a blog post saying, in part:
- We have carefully reviewed our records and can confirm that there was a failed attempt made to gain this customer’s information by contacting PayPal.
- PayPal did not divulge any credit card details related to this account.
- PayPal did not divulge any personal or financial information related to this account.
- This individual's PayPal account was not compromised.
This obviously contradicts the attacker's version of his contact with PayPal. The attacker told Hiroshima the following:
I called paypal and used some very simple engineering tactics to obtain the last four of your card (avoid this by calling paypal and asking the agent to add a note to your account to not release any details via phone)
GoDaddy’s response
When Ars contacted GoDaddy to get its version of what happened, the company's PR group responded with a prepared statement from Todd Redfoot, its chief information security officer:
Our review of the situation reveals that the hacker was already in possession of a large portion of the customer information needed to access the account at the time he contacted GoDaddy. The hacker then socially engineered an employee to provide the remaining information needed to access the customer account. The customer has since regained full access to his GoDaddy account, and we are working with industry partners to help restore services from other providers. We are making necessary changes to employee training to ensure we continue to provide industry-leading security to our customers and stay ahead of evolving hacker techniques.
Here, GoDaddy corroborates some elements of the attacker's explanation—copping to a successful social engineering attempt and confirming access to the account was granted to the attacker. However, GoDaddy also points out that the attacker "was already in possession of a large portion of the customer information needed" to access Hiroshima's account.
Wither Twitter?
Twitter has not made any statements on the attack other than to say that it is still investigating. Wednesday afternoon, the Twitter page for @N showed that the account was private; by the evening, the account appeared to have been deleted (whether by the attacker or by Twitter is unclear). However, as of right now, the handle @N displays the name "Follow Badal_NEWS" (and @badal_news currently appears to be a private account).
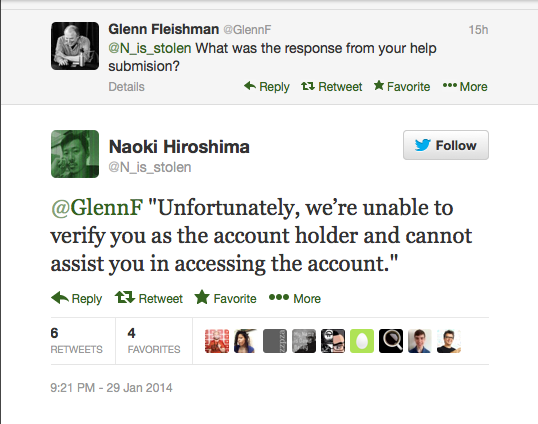
Hiroshima (under his updated @N_is_stolen handle) continues to tweet, noting that the response he has received from Twitter so far has been that it is unable to help:
What about the feds?
The comment thread from yesterday contained no small number of Ars users suggesting that Hiroshima should contact the FBI—when words like "extortion" get thrown around, contacting the FBI seems like a logical course of action.
There are a tremendous number of factors involved, however—not the least of which being that it's unclear whether the attacker is based in the US. Additionally, there's the question of the value of the item—if it were a briefcase full of $50,000 in cash, the value would be clear, but we're talking about a Twitter handle. How does a law enforcement official assess the value of that? No violence or threat of violence was used to acquire the @N handle, so there was no traditional robbery.Hiroshima had two-factor authentication enabled on many of the accounts in question, ostensibly making them more secure—but it didn't help even a little bit.
On the other hand, it does seem obvious that some kind of crime occurred—theft of identity and something under the "computer crime" blanket; there's also that "extortion" label.
Ars reached out to the FBI to comment, and Bureau media spokesperson Paul Bresson responded that while he had not yet heard the details of Hiroshima's story, "we encourage anyone who believes they have been extorted or a victim of a crime to contact us. We can gather the facts to determine if a federal violation has occurred and thus investigate further or otherwise refer to another appropriate agency for necessary follow-up."
Ars has been attempting to follow up with the FBI, but as of press time, we have not heard back.
What happened, and what can you do?
There were two avenues down which the attack against Hiroshima's accounts proceeded: electronic and social. We'll tackle them one at a time, but the cynical answer—based on this and many other incidents, including a very similar one two years ago in which Wired writer Mat Honan lost access to his own short Twitter account, @mat—is that if you're targeted by a sufficiently motivated attacker, you will almost certainly lose.
First, though, the electronic. Most websites allow password resets via e-mail, and so gaining access to a victim's e-mail account and then resetting their password is one way to gain access to other things. In this case, the attacker attempted to take over Hiroshima's e-mail not by guessing a password but by changing the destination to which Hiroshima's e-mail was delivered.
This is worth a bit of explanation, because even to a lot of savvy Internet users, e-mail is kind of a black box. It's like running water or electric lights—you don't often think about how or why it works. In order to send e-mail from me to you, though, I must have a way of knowing what e-mail server your inbox lives on (or, at least, my e-mail server does). This information is provided by special DNS records called "MX records" (short for Mail eXchange). In order for an Internet domain like arstechnica.com to be able to receive e-mail, that domain must have valid MX records. Here's ours, for example, which you can look up using the dig tool:
$ dig arstechnica.com -t MX ... ;; QUESTION SECTION: ;arstechnica.com. IN MX ;; ANSWER SECTION: arstechnica.com. 3227 IN MX 0 d11979a.ess.barracudanetworks.com.
Since we use Barracuda for spam filtering, our domain's MX record points at d11979a.ess.barracudanetworks.com as the delivery server.
Hiroshima has his own domain, h7a.org, registered through GoDaddy. E-mail for addresses ending in "@h7a.org" is provided by Google through its Google Apps service (which, until December 2012, had a free tier usable by anyone who wanted custom domain e-mail hosting, among other services). The MX records for h7a.org correctly show Google-owned e-mail servers:
$ dig h7a.org -t MX ... ;; QUESTION SECTION: ;h7a.org. IN MX ;; ANSWER SECTION: h7a.org. 86029 IN MX 50 aspmx4.googlemail.com. h7a.org. 86029 IN MX 60 aspmx5.googlemail.com. h7a.org. 86029 IN MX 0 aspmx.l.google.com. h7a.org. 86029 IN MX 10 alt1.aspmx.l.google.com. h7a.org. 86029 IN MX 20 alt2.aspmx.l.google.com. h7a.org. 86029 IN MX 30 aspmx2.googlemail.com. h7a.org. 86029 IN MX 40 aspmx3.googlemail.com.
GoDaddy is the registrar for h7a.org, so the attacker got into Hiroshima's GoDaddy account and altered h7a.org's MX records. Instead of pointing at Google's mail servers, mail sent to *@h7a.org was routed to the attacker's own server or servers. That way, the attacker could have Facebook or Twitter send password reset e-mails to Hiroshima's e-mail address; those e-mails would be sent directly to an inbox set up by the attacker.
In his write-up, Hiroshima laments his use of his own e-mail domain for registering at services like Facebook and Twitter, saying that the use of a Gmail address or something similar would have kept the attacker from using this method to gain access to his Facebook account, among other things. This is true—but it's also throwing the baby out with the bathwater.
Hiroshima is correct in the sense that it's extremely unlikely that anyone would convince a registrar to transfer ownership of google.com or gmail.com or googlemail.com or any clearly Google-owned domain. However, lacking that tactic, an attacker could fall back on more traditional password compromise methods for the Gmail account—likely starting with password reuse from other compromised places. On the other hand, even with a personal domain registrar to compromise, password hacking is still an option. It all becomes a question of how much work the attacker is willing to put into the job.
In this particular case, though, the attempt to hijack Hiroshima's MX records was temporarily stymied by the DNS TTL—the "time to live" setting on the records themselves. DNS is a hierarchical thing, and looking up a single IP address can involve a number of queries to a number of different DNS servers; in order to keep DNS traffic down, records include a TTL setting to tell requesting computers how long to cache a particular record before querying the authoritative DNS server again. Hiroshima's attacker hijacked his MX records, but the records' TTL setting prevented mail from immediately flowing to the attacker. However, this was only a temporary setback because the attacker had additional tools at his disposal—including ultimately just contacting Hiroshima and threatening to delete his GoDaddy-hosted websites.
Many registrars—GoDaddy included—offer two-factor authentication for accounts. This method requires you to enter not just a password but an additional code from a smartphone, keyfob, or an application on your computer. Hiroshima had two-factor authentication enabled on many of the accounts in question, ostensibly making them more secure—but it didn't help even a little bit.
Why? Because people are agreeable.
Reader Comments (155)
View comments on forumLoading comments...