
Independent security journalist Brian Krebs has uncovered important new details about the hack that compromised as many as 110 million Target customers, including the malware that appears to have infected point-of-sale systems and the way attackers first broke in.
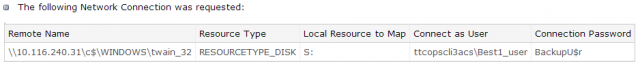
According to a post published Wednesday to KrebsOnSecurity, point-of-sale (POS) malware was uploaded to Symantec-owned ThreatExpert.com on December 18, the same day that Krebs broke the news of the massive Target breach. An unidentified source told Krebs that the Windows share point name "ttcopscli3acs" matches the sample analyzed by the malware scanning website. The thieves used the user name "Best1_user" to log in and download stolen card data. Their password was "BackupU$r".
The class of malware identified by Krebs is often referred to as a memory scraper, because it monitors the computer memory of POS terminals used by retailers. The malware searches for credit card data before it has been encrypted and sent to remote payment processors. The malware then "scrapes" the plain-text entries and dumps them into a database. Krebs continued:
According to a source close to the investigation, that threatexpert.com report is related to the malware analyzed at this Symantec writeup (also published December 18) for a point-of-sale malware strain that Symantec calls "Reedum" (note the Windows service name of the malicious process is the same as the ThreatExpert analysis "POSWDS"). Interestingly, a search in Virustotal.com—a Google-owned malware scanning service—for the term “reedum” suggests that this malware has been used in previous intrusions dating back to at least June 2013; in the screen shot below left, we can see a notation added to that virustotal submission, “30503 POS malware from FBI."
The source close to the Target investigation said that at the time this POS malware was installed in Target's environment (sometime prior to November 27, 2013), none of the 40-plus commercial antivirus tools used to scan malware at virustotal.com flagged the POS malware (or any related hacking tools that were used in the intrusion) as malicious. “They were customized to avoid detection and for use in specific environments,” the source said.
That source, and one other involved in the investigation who also asked not to be named, said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system.
According to the author of BlackPOS—an individual who uses a variety of nicknames, including “Antikiller”—the POS malware is roughly 207 kilobytes in size and is designed to bypass firewall software. The barebones “budget version” of the crimeware costs $1,800, while a more feature-rich “full version”—including options for encrypting stolen data, for example—runs $2,300.
Krebs went on to report that sources told him the attackers broke into Target after hacking a company Web server. From there, the attackers somehow managed to upload the POS malware to the checkout machines located at various stores. The sources said the attackers appeared to then establish a control server inside Target's internal network that "served as a central repository for data hoovered by all of the infected point-of-sale devices." The attackers appear to have had persistent access to the internal server, an ability that allowed them to periodically log in and collect the pilfered data.
The details haven't been independently verified by Ars. That said, Wednesday's report is consistent with what's already known about the compromise. For instance, last week's news that the attackers also made off with names, mailing addresses, phone numbers, and e-mail addresses of Target customers already suggested the hackers had intruded deep inside Target's network and that the point-of-sale malware was just one of the tools used to extract sensitive data. Word that the intruders gained initial access through Target's website is also consistent with what's known about previous hacks on large holders of payment card data. Court documents filed in 2009 against now-convicted hacker Albert Gonzalez said one of the ways his gang compromised Heartland Payment Systems, as well as retailers 7-Eleven and Hannaford Brothers, was by casing their websites and exploiting SQL-injection vulnerabilities.
Reader Comments (104)
View comments on forumLoading comments...