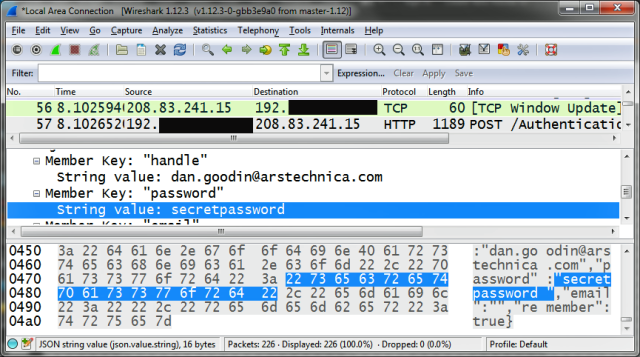
Tens of millions of Match.com subscribers risk having their site password exposed each time they sign in because the dating site doesn't use HTTPS encryption to protect its login page.
The screenshot above was taken Thursday afternoon. Showing a session from the Wireshark packet sniffing program, you can see that this reporter entered "dan.goodin@arstechnica.com" and "secretpassword" into the user name and password fields of the Match.com login page.
Amazingly, the page uses an unprotected HTTP connection to transmit the data, allowing anyone with a man-in-the-middle vantage point—say, someone on the same public network as a Match.com user, a rogue ISP or telecom employee, or a state-sponsored spy—to pilfer the credentials. Had Match.com followed basic security practices and properly enabled HTTPS on the login page, the entire session would have been unintelligible to all but the end user and connecting server.
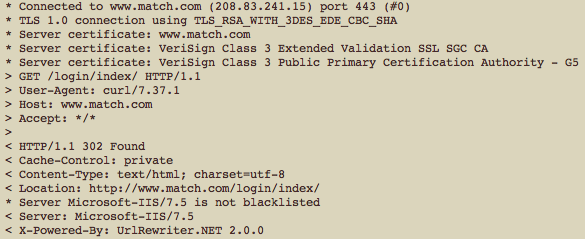
Ars reader Scott Bryner, who alerted Ars to the Match.com faux pas, said he first noticed it in early March. It's unclear exactly how long the site has failed to encrypt user credentials. Bryner provided the screenshot immediately above this paragraph, which suggests Match.com is experiencing a server configuration error that's redirecting all HTTPS traffic to an HTTP connection. As a site with tens of millions or possibly hundreds of millions of members, that's a lot of password exposure. Ars has asked Match.com officials for comment and will update this post if they respond.
reader comments
41