
On Verizon Wireless’ website, the company advises customers to “[n]ever give your passwords to anyone over the phone, include them in e-mail messages, [or] give them to anyone.” This is good security advice that experts would agree with. Yet Verizon itself is seeking out customers on Twitter and asking for their billing passwords over the social network’s direct messages platform.
This, obviously, isn’t the best security practice. Security experts who spoke to Ars disagreed on just how dangerous it is but agreed that Verizon should find a better way to verify the identities of customers.
It’s not a new strategy for Verizon, but I wasn’t aware of it until this week when the Verizon Wireless customer support account inserted itself into a Twitter conversation I was having, urged me to follow the account so we could exchange direct messages, and then asked for my mobile number and billing password. (Note: The billing password is akin to a PIN and separate from a customer's primary account password, but I didn't know that because Verizon's customer service account did not make this clear to me, and it seems likely other customers could be confused as well.)
This started when I was discussing the phone unlocking policies of AT&T and Verizon on Twitter, even though I wasn't trying to contact Verizon's Twitter account. If you’re a Twitter user, you know that the way to get a company’s attention is to write a tweet with the company’s account name and an @ in front of it. I didn't do that—the Verizon account found me not because I wanted it to, but because an employee operating it must have been searching Twitter for any mentions of the company's name in order to drum up new business. Verizon’s first tweet to me was, “We hold the key to unlocking the best wireless experience on that iPhone! We would love to have you w/us.”
I informed the account that I’m already a Verizon customer but that I’d be interested in getting tethering added to my account without having to pay a lot more. (To make a long story short: I have a cheaper, grandfathered plan that doesn’t include tethering.) Verizon responded, “Let's take a look and see what plans (maybe even promotions) fit your needs the most. Please follow and DM [direct message] us.”
“Why would you need my password?”
I did, and after exchanging a couple of messages about my monthly plan, the account said, “Got it, lets take a closer look and find the best option! What's your mobile number & Billing Password to access the details?”
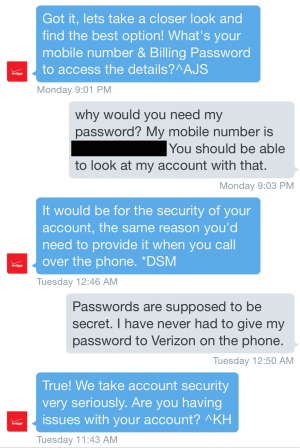
You can see in the above screenshot that there are different initials appended to each message, meaning each response came from a different Verizon employee. The last response from “KH” seems to come from someone who hadn’t read the previous messages and thus didn’t understand the context of the conversation.
Subsequently, through e-mails I exchanged with Verizon’s public relations team and a look at my own account online, I found out that the “billing password” Verizon asked me for is different from the only password I had ever set up with the company. By default, it’s the last four digits of your social security number, but it can be changed to a four- or five-character PIN.
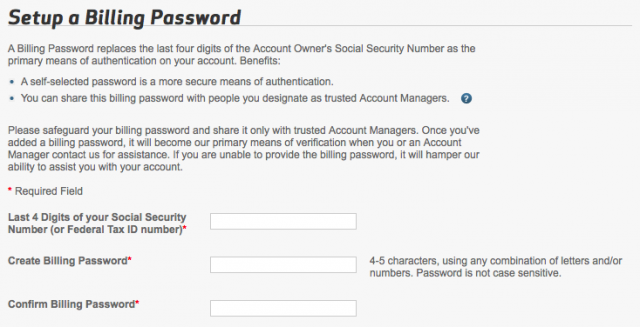
Had I decided to give my password to the Verizon account over Twitter DM, I would have supplied the only password I knew I had, the much longer, more complex one I use to log into my account online. The Verizon Twitter account didn’t explain the difference to me. It seems other Verizon customers have been surprised by this request as well:
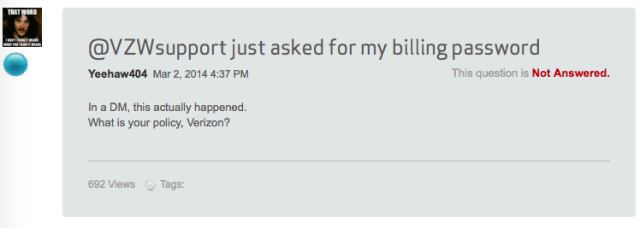
Lmfao a verizon rep asked for my billing password in a DM
— DESTROYMAN (@topbunkwanter) May 8, 2014
(This is a bit off topic, but I also came across a thread from 2009 in which a customer reported that a Verizon technician asked for the customer's Gmail password.)
How risky is this? Experts weigh in.
A Verizon spokesperson told Ars that Verizon employees who receive billing passwords over Twitter DM “see the same account information as a rep who helps a customer in a store or over the phone.”
“DMing your password to someone essentially shotguns it all over the place in plain text.”
If Verizon communicated with customers in a less confusing manner, this system wouldn’t be so different from using a PIN over the phone to authenticate yourself to a customer service representative. But there are a few legitimate concerns.
Security expert Troy Hunt warned about the dangers of sending passwords over DM in 2012, saying they “likely result in transmission over insecure medium.”
Companies that handle lots of customer passwords obscure them through processes known as hashing and salting, so that even if a password database leaks, hackers have to do a lot of extra work to convert the passwords to plain text. Sending passwords over direct messages raises the possibility that the passwords could leak in an unobscured form, albeit in smaller quantities than in a password database containing thousands or millions of credentials.
Twitter direct messages can’t be seen publicly by everyone like regular tweets, but Twitter abandoned a plan to encrypt direct messages earlier this year.
“Direct messages are not a form of secure communication,” password security consultant Jeremi Gosney of Stricture Consulting Group told Ars. “I’m not sure why anyone would ever think it was. Yes, Twitter DMs are sent over HTTPS, but Twitter does not employ end-to-end encryption, and there is no evidence that DMs are stored encrypted, so now your password is sitting in Twitter's database in plain text. DMs are also e-mailed to the recipient, and while Twitter recently rolled out STARTTLS support, it must be supported by both parties, and a lot of mail servers still don't support it, so your password is likely e-mailed in plain text as well. It's also sitting on the mail server in plain text, and unless the recipient is using webmail, a copy of the message is downloaded to the recipient's computer, laptop, phone, or all three, again in plain text. In other words, DMing your password to someone essentially shotguns it all over the place in plain text. You are creating a mess that you are powerless to clean up.”
The fact that Verizon wants a different password than a customer’s main account password makes the practice “not as bad,” Gosney said, “though it is still open to interception and someone could still call VZW and supply the billing password and make unauthorized changes to your account. People are easier to manipulate than computers, especially if you have the phone password.” Plus, because of Verizon’s poor communication, “I’m sure lots of people send their account password first, and they have to go ‘no, not that password, your other password.’”
Per Thorsheim, a security expert who organizes the annual PasswordsCon conference, doesn’t think Verizon’s DM password requests are quite as bad as Gosney does, but Thorsheim also said the fact that Verizon is asking for a “billing password” rather than an account password doesn’t excuse the poor behavior.
“Twitter has really good HTTPS configuration, so your verification password sent by Twitter DM really isn't at the risk of being eavesdropped,” Thorsheim told Ars. “That said: your account could be hijacked, but the attack doesn't scale that way. The correct question to ask is this: what could happen if the Twitter account of Verizon (@VZWSupport) got hacked? That would be a nice history of DMs with passwords.”
There is a good chance Verizon isn’t securing its customer support Twitter account with Twitter’s two-factor authentication, because it is far easier to enable for a single user than for multiple users sharing a single account. We’ve asked Verizon if it has enabled two-factor on the account but haven’t received an answer.
Teaching customers poor security practices lowers their defenses
Another risk has to do with educating users about proper password practices. As we noted at the beginning of this article, Verizon itself advises customers not to give out passwords over e-mail. Yet by asking for billing passwords over Twitter DM, Verizon is teaching customers that sometimes it’s ok to type passwords into forms other than a login screen. Most people aren’t security experts, and many computer users lack basic security savvy. Encouraging people to give out passwords over mediums like Twitter DM could lower their defenses, opening them to phishing attacks from malicious actors.
“I don't see this as a major risk to either Verizon or their customers, but personally I would recommend figuring out some other way of verifying the account owner upon contact,” Thorsheim said.
In terms of teaching people to be wary of threats like phishing, “I’m tempted to say that Verizon is contributing to the problem and not the solution in this case," he said.
Verizon’s spokesperson didn’t answer all of my questions but provided some general information about why the company asks customers for billing passwords on Twitter. Verizon said:
Our customer service team looks into questions customers may have about their account. The team tries to answer as many questions as they can in public fashion through @ twitter replies. There are cases though where a specific question requires the customer service rep to look into the matter at the account level. That is when the rep will reach out to the customer and confirm the mobile number on the account. If the account has a billing password that the customer set up, the rep will then ask for it for validation and security purposes. The same practice is done if a customer calls in to customer service and the inquiry requires looking into the case at the account level. This is a standard policy we have implemented across the board.
As for whether Verizon asking for passwords over DM conflicts with the company’s own security advice, Verizon said, “[w]e still continue to encourage customers to be cautious online and always practice safe practices online with their personal information. Our Twitter account is verified and only managed by Verizon Wireless reps. If a customer does not feel secure about sharing their billing system password/pin over twitter, they are more than welcome to express that to the rep over DM and elect to have the rep contact them over the phone. We’re giving customers another option to reach out to us for their questions and concerns.”
reader comments
85