Hundreds of websites running WordPress or Joomla content management systems (CMS) have been attacked for five months now with malicious SWF files that inject hidden iframe code.
The code is then used to direct the browser to a location hosting malware (such as an exploit kit) and deliver it to the visitor’s computer.
Malicious SWF is one pixel in size
SWF files are used for creating rich Internet applications that can be executed in Adobe Flash Player. As such, an outdated version of the product is susceptible to attacks that exploit vulnerabilities.
The campaign was identified in early November last year, and initially, Joomla websites were mostly seen to be affected, but evidence has recently emerged that the attacker also targets servers running WordPress.
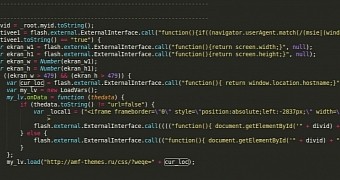
The bad SWF, which is only one pixel large, is added to the site’s “images/banners/” folder and its name is a set of three random characters, with an identification number appended.
Security solutions added detection
Peter Gramantik, senior security researcher at Sucuri, says that based on the similarities (variable names, coding logic, and UserAgent condition) observed, the same threat actor is at work, although in the latest recorded incidents the malicious payload is delivered from a different source than in November.
Also, a larger number of websites is impacted by the current operation, with an estimate of at least several hundreds.
On the bright side of things, this time around the malicious file is detected by a lot more antivirus products than before.
A scan on Virus Total shows that 23 out of 57 solutions are currently flagging the threat, which is a significant improvement, considering that at the beginning of the campaign, the nasty SWF went completely undetected.
The researcher says that, because malware is evolving continuously, variations of the malicious file are expected in the future.
 14 DAY TRIAL //
14 DAY TRIAL //